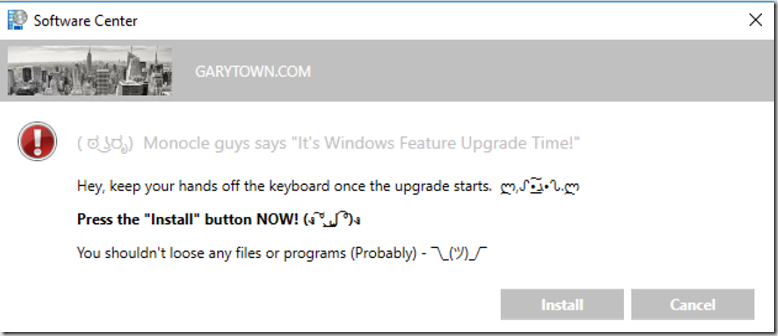
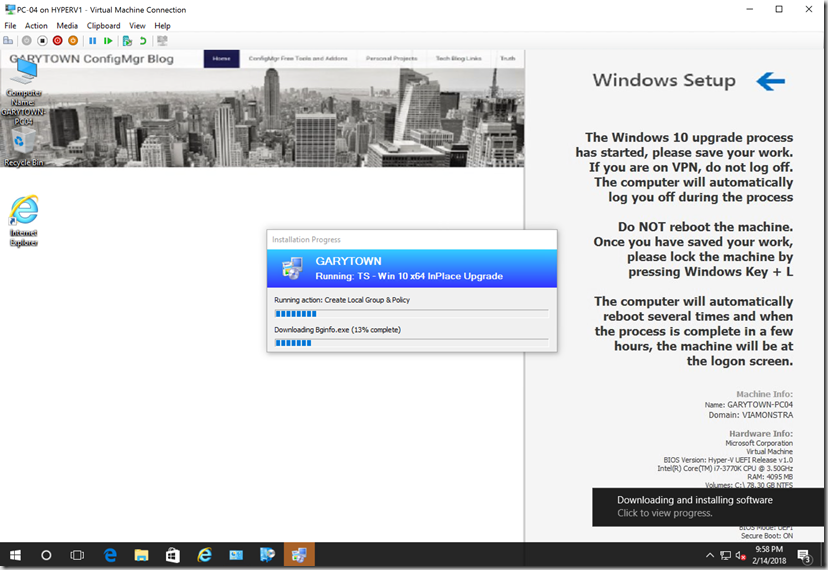
{
I thought that was a clever title, but it seems more confusing the longer I look at it… anyway, this is the follow up post to take BGinfo from MDT, and add it’s capabilities to the ConfigMgr In-Place Upgrade Task Sequence Process. If you’ve been working with in-place upgrade task sequences, you’ll know they are a different beast than regular OSD. You can’t just call an application and expect it to show up on the screen.. like in OSD, you can say Command Line Step: notepad.exe… and guess what, a notepad.exe window opens during the TS.. freaking amazing!
Windows 10
Bitlocker on Hyper-V Virtual Machine
Updates 2020.02.27:
Two great posts you should check out from Niall
- Enabling Full Disk Encryption in Microsoft Endpoint Configuration Manager 1910 in a task sequence
- Full disk encryption (in ConfigMgr 1910) – a closer look on real hardware
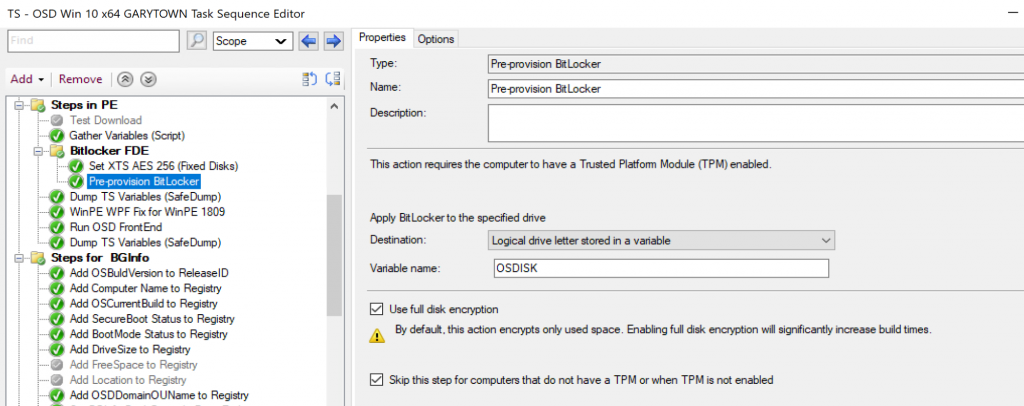
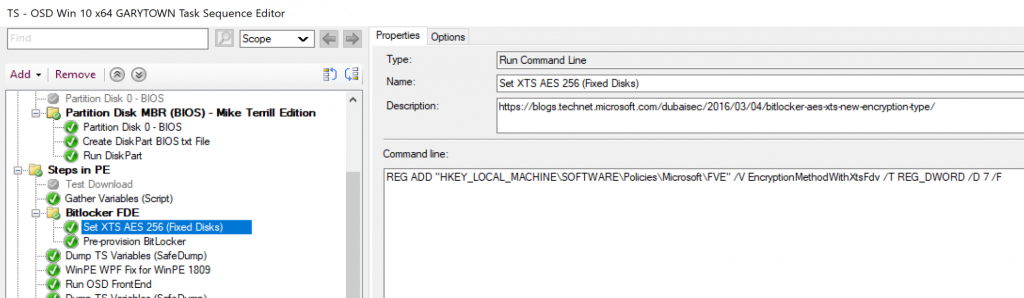
Wanted to point out, if you pre-provision bitlocker, currently (1910) and you want to use XTS 256 instead of the default 128, you NEED to set a registry key first.
REG ADD “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE” /V EncryptionMethodWithXtsFdv /T REG_DWORD /D 7 /F
Upate 2017.11.29 – Thanks to Paul Smith @MrPRSmith for the idea, I was able to get FDE working using a pass-through disk, see bottom of post for more info.
Short post to go over something I found while researching Bitlocker Full Disk Encryption on Hyper-V virtual machines.
I was testing Enabling Bitlocker during our Task Sequence, and I didn’t have any physical machines to test on, no problem right? With Hyper-V, you can now enable virtual TPM on Gen2 VMs, and have all the yummy goodness of UEFI, Secureboot, Bitlocker, Credential Guard all on your VM! So I started testing, everything worked! But when I checked the Bitlocker Status (manage-bde –status), it showed I was only encrypting Used Space. While this would be fine for a Virtual Machine, I was confused because I told it to use Full Disk, NOT used space. I ran many tests, trying several different things, but in the end, it never came out as I expected, with Full Disk. Even post OSD, if I decrypted, ensured policy was set for Full Disk, it would only encrypt Used Space. Finally, I gained access to a physical test machine, ran the exact same Task Sequence, and there it was, Full Disk Encryption. – Testing done on Hosts: Win 10 1607, 1709 & Server 2016. VM’s running 1703 and 1709. Security settings were set to Enable Secure Boot & Enable TPM, tested Dynamic expanding & fixed disks. (Not Pass-through)
Clean Up Storage Pre Upgrade
Just another group of tasks to add to your arsenal. We run a Check Readiness step before our upgrades, with a minimum of 20GB Free. We have many clients that do not meet this minimum requirement and fail, and then have to remediate. While we have long term plans to automate much of this, and prevent the Task sequence from ever running on machines that don’t reach these pre-reqs, for now, a Band-Aid.
ConfigMgr Task Sequence Collection
This is my “Clip Show” blog post, but hopefully you still find it useful.
I’ve been building out a Task Sequence that is just a collection of Task Sequence sections, or handy steps. I’ll use this TS to pull sections from when I create new Task Sequences, and add / modify as I test in “Real” deployment Task Sequences. DOWNLOAD HERE *Note, this is not an actual Deployment TS, it’s meant to be imported and then have parts copied into your own TS. All content, including some not used directly in this TS is included.
Change Lock Screen & lockout users during Upgrade TS
Update 2017.10.26 – After a twitter convo with @brookspeppin, I added two additional steps for the legal notice. I had ones to delete them, but Brooks said he had used them as the upgrade message, skipping everything else. This was something I had considered, but after talking it over with the team, decided against it “No one reads that”, but after seeing Brooks’ screen capture, I tend to agree that it’s worth having in your pocket, so I’ve added it to the Task Sequence Export that’s available to download. Here is a screen capture and keys needed.