Updates 2020.02.27:
Two great posts you should check out from Niall
- Enabling Full Disk Encryption in Microsoft Endpoint Configuration Manager 1910 in a task sequence
- Full disk encryption (in ConfigMgr 1910) – a closer look on real hardware
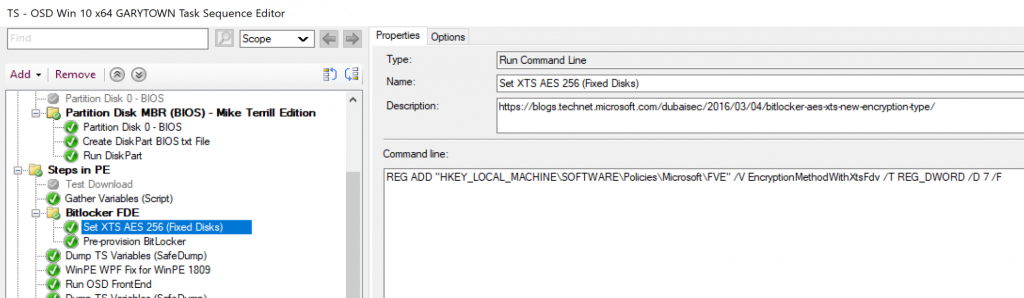
Wanted to point out, if you pre-provision bitlocker, currently (1910) and you want to use XTS 256 instead of the default 128, you NEED to set a registry key first.
REG ADD “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE” /V EncryptionMethodWithXtsFdv /T REG_DWORD /D 7 /F
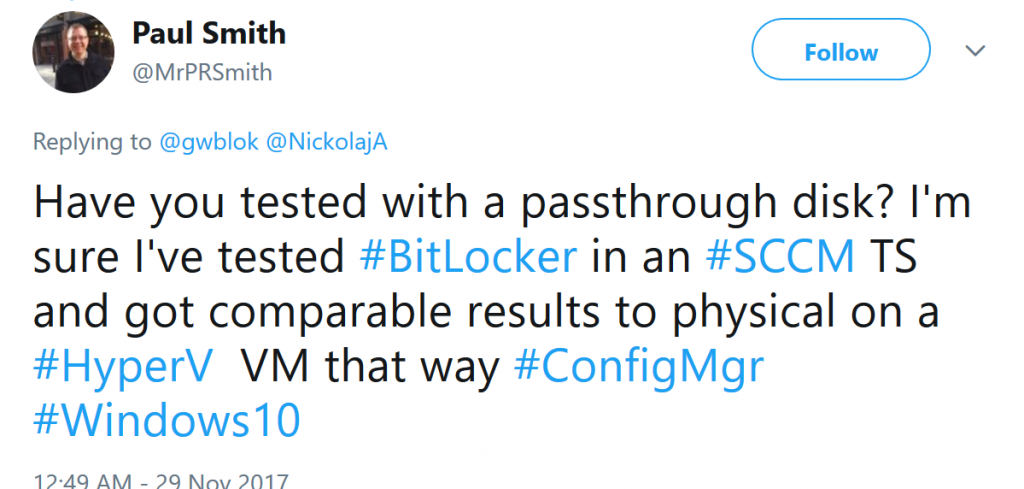
Upate 2017.11.29 – Thanks to Paul Smith @MrPRSmith for the idea, I was able to get FDE working using a pass-through disk, see bottom of post for more info.
Short post to go over something I found while researching Bitlocker Full Disk Encryption on Hyper-V virtual machines.
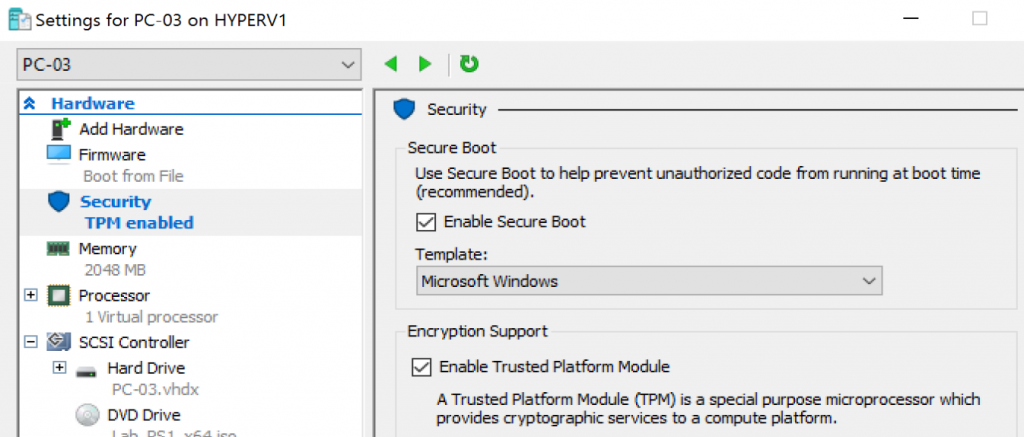
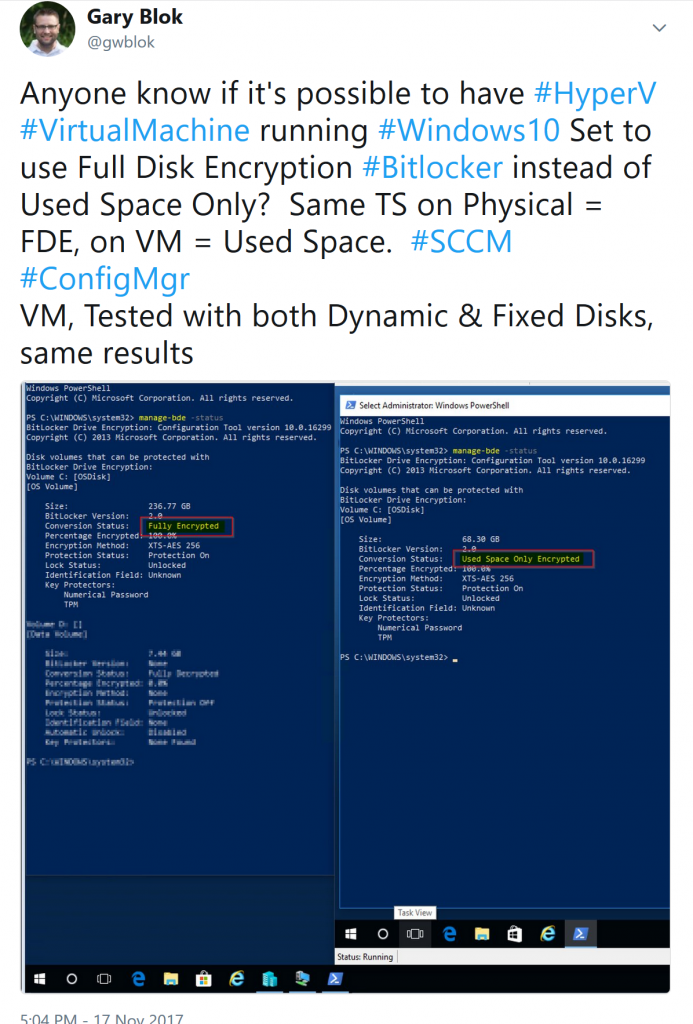
I was testing Enabling Bitlocker during our Task Sequence, and I didn’t have any physical machines to test on, no problem right? With Hyper-V, you can now enable virtual TPM on Gen2 VMs, and have all the yummy goodness of UEFI, Secureboot, Bitlocker, Credential Guard all on your VM! So I started testing, everything worked! But when I checked the Bitlocker Status (manage-bde –status), it showed I was only encrypting Used Space. While this would be fine for a Virtual Machine, I was confused because I told it to use Full Disk, NOT used space. I ran many tests, trying several different things, but in the end, it never came out as I expected, with Full Disk. Even post OSD, if I decrypted, ensured policy was set for Full Disk, it would only encrypt Used Space. Finally, I gained access to a physical test machine, ran the exact same Task Sequence, and there it was, Full Disk Encryption. – Testing done on Hosts: Win 10 1607, 1709 & Server 2016. VM’s running 1703 and 1709. Security settings were set to Enable Secure Boot & Enable TPM, tested Dynamic expanding & fixed disks. (Not Pass-through)
To Summarize.
- Hyper-V Virtual Machine = Used Space Encryption only with Bitlocker *Unless you can use a pass-though disk.
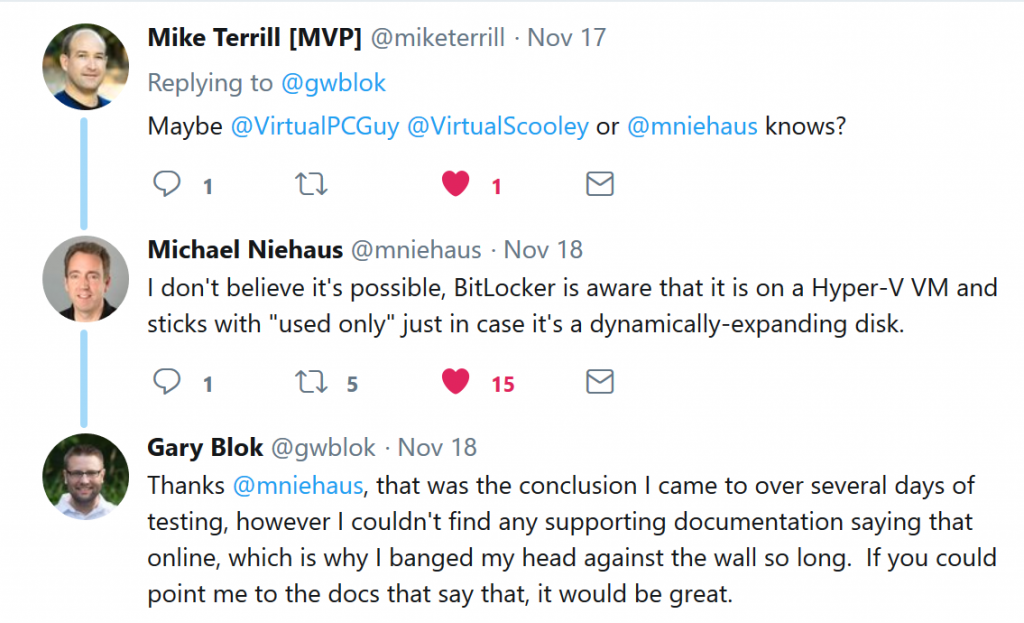
- This is by Microsoft Design, Bitlocker is “Hyper-V Aware” and will only run in Used Space only mode, even if your policy is set for Full Disk
- Remember to eject your ISO you booted from before the Bitlocker steps, or it will error
- If you need to test your Full Disk Encryption OSD settings, do it on a physical machine. – Below I have two screen captures side by side. Left side = Physical Machine & right side = VM on that Physical Machine. Both machines ran same TS telling it to use FDE, but only the Physical machine actually used FDE.
How do you change your TS from doing Used Space to Doing Full Disk?
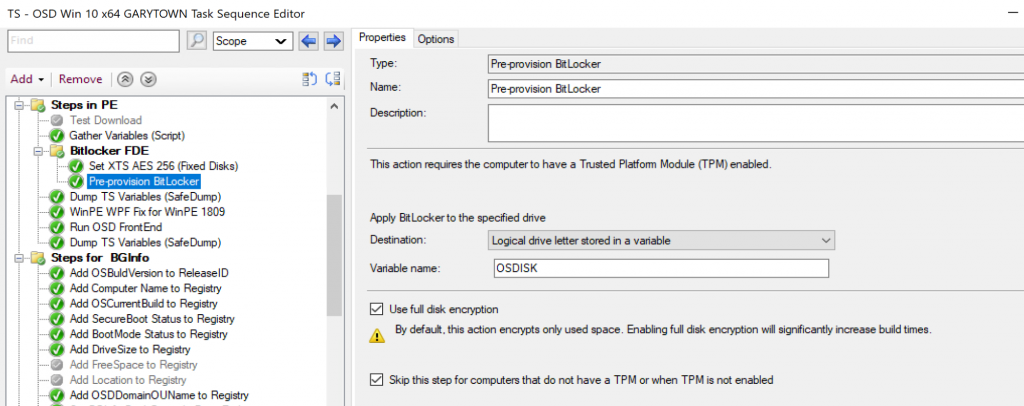
- Disable the Pre-Provision Bitlocker Steps
- Add Registry key to set Full Disk Encryption before “Enable Bitlocker” Step.
- Set “Enable-Bitlocker” step to Continue on Error
- This will set several policies settings, like save the key to AD, and which way you want to deploy bitlocker (TPM only, etc)
- Add Additional Manage-Bde Step: manage-bde -on C: -RecoveryPassword
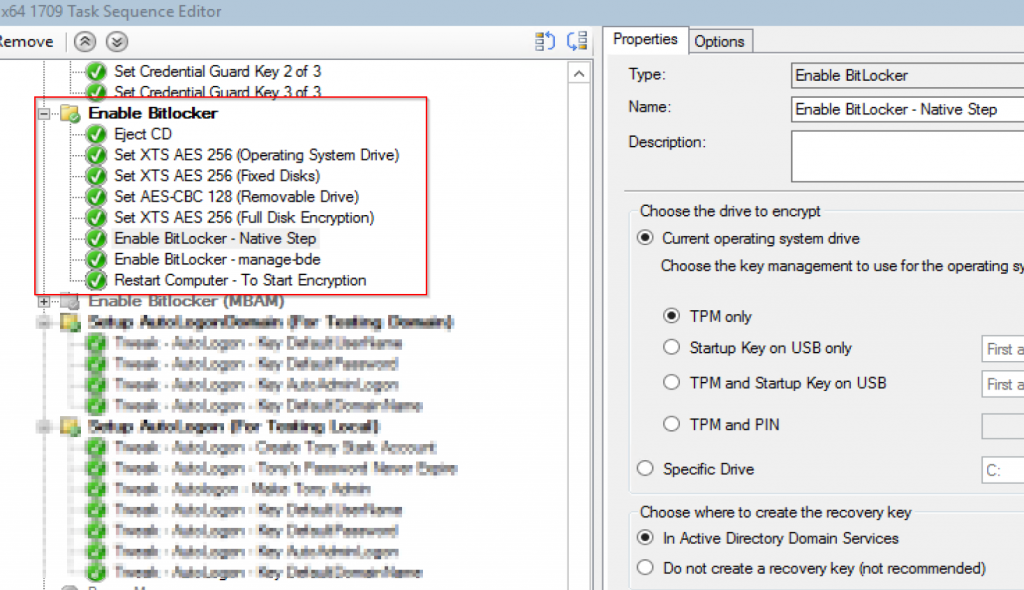
Here are the details for the steps in my TS, as you can see, I also set it to use XTS AES 256 (except for flash media, which I use older type so it’s more backwards compatible with other Windows computers)
Eject CD
powershell.exe -NoProfile -Command "(New-Object -ComObject 'Shell.Application').Namespace(17).Items() | Where-Object { $_.Type -eq 'CD Drive' } | foreach { $_.InvokeVerb('Eject') }"
Set XTS AES 256 (Operating System Drive)
REG ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE" /V EncryptionMethodWithXtsOs /T REG_DWORD /D 7 /F
Set XTS AES 256 (Fixed Disks)
REG ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE" /V EncryptionMethodWithXtsFdv /T REG_DWORD /D 7 /F
Set AES-CBC 128 (Removable Drive)
REG ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE" /V EncryptionMethodWithXtsRdv /T REG_DWORD /D 3 /F
Set XTS AES 256 (Full Disk Encryption)
REG ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE" /V OSEncryptionType /T REG_DWORD /D 1 /F
Enable BitLocker - manage-bde
manage-bde -on c: -RecoveryPassword
2017.11.29 – Getting FDE to work using Pass-Though
Using an Offline Disk on the Host, and setting that as the drive on the VM, FDE works.
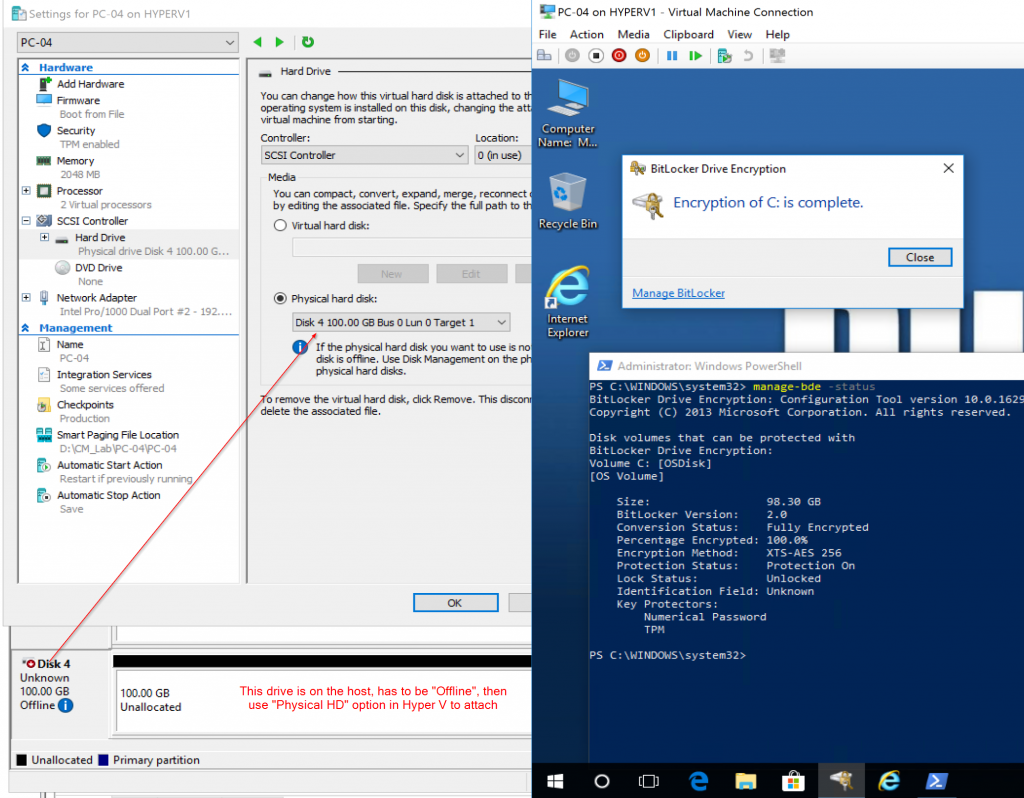
Thanks Paul, can now test FDE on VM!
Thank you for this post!
I’m trying this in MDT, the full disk encryption method needs to be done within the OS right? I got an error when trying this manually in WinPE.
Yes, Bitlocker is configured for Windows once Windows is loaded and you’re booted into the OS. You can do it anytime after the “Install & Configure the Configuration Manager Client” step. It typically add it near the end, but you can really do it anytime once the TS is running in the OS and not WinPE.
You can now setup Full Disk Encryption during WinPE in the TS. Unsure when this changed, or if I was just always wrong. 🙂
Hello Gary,
Can you please provide me details on TS step Enable bitlocker – manage-bde ? Im not sure how to set this step.
Thank you
Mike
In the post, there is a section that lists the steps and commands. However in the latest CM (2002), this is no longer needed. (manage-bde step).
In my latest test on my VM, the native step worked perfectly with the changes they have made.
I’ll try to update my post eventually, but you should play with the native step a bit as it should do what you want.