Updates 2020.02.27:
Two great posts you should check out from Niall
- Enabling Full Disk Encryption in Microsoft Endpoint Configuration Manager 1910 in a task sequence
- Full disk encryption (in ConfigMgr 1910) – a closer look on real hardware
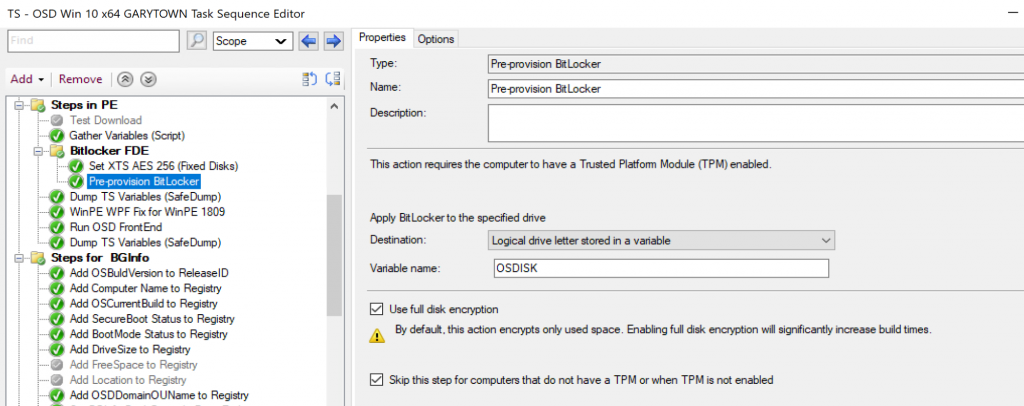
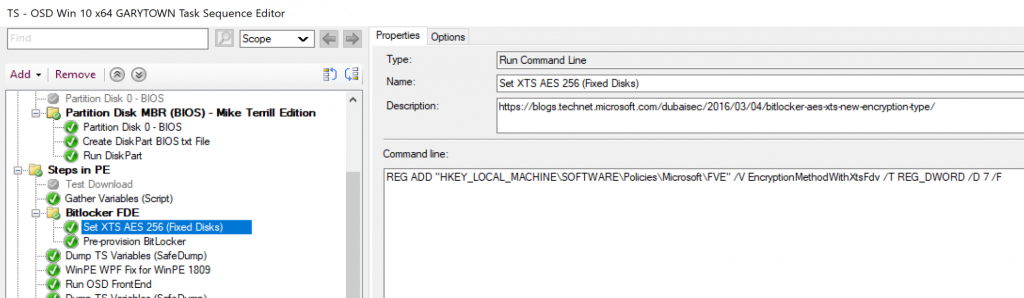
Wanted to point out, if you pre-provision bitlocker, currently (1910) and you want to use XTS 256 instead of the default 128, you NEED to set a registry key first.
REG ADD “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE” /V EncryptionMethodWithXtsFdv /T REG_DWORD /D 7 /F
Upate 2017.11.29 – Thanks to Paul Smith @MrPRSmith for the idea, I was able to get FDE working using a pass-through disk, see bottom of post for more info.
Short post to go over something I found while researching Bitlocker Full Disk Encryption on Hyper-V virtual machines.
I was testing Enabling Bitlocker during our Task Sequence, and I didn’t have any physical machines to test on, no problem right? With Hyper-V, you can now enable virtual TPM on Gen2 VMs, and have all the yummy goodness of UEFI, Secureboot, Bitlocker, Credential Guard all on your VM! So I started testing, everything worked! But when I checked the Bitlocker Status (manage-bde –status), it showed I was only encrypting Used Space. While this would be fine for a Virtual Machine, I was confused because I told it to use Full Disk, NOT used space. I ran many tests, trying several different things, but in the end, it never came out as I expected, with Full Disk. Even post OSD, if I decrypted, ensured policy was set for Full Disk, it would only encrypt Used Space. Finally, I gained access to a physical test machine, ran the exact same Task Sequence, and there it was, Full Disk Encryption. – Testing done on Hosts: Win 10 1607, 1709 & Server 2016. VM’s running 1703 and 1709. Security settings were set to Enable Secure Boot & Enable TPM, tested Dynamic expanding & fixed disks. (Not Pass-through)