If you have HP Devices (and you should), you probably have used HPIA. HPIA is a tool that will scan your computer for updates and other recommendations and apply them (and it will do a lot more). This tool has extensive command line parameters, which I like. Check out the User Guide’s Command Line area.
I use HPIA in a lot of my solutions, even written a module for OSDCloud to update HP Devices. For now though, I’m using in in a Run Script… pushing the limits of the Run Script.
You can grab the Script on my GitHub: Run-HPIA.ps1
Related: How To Create List of Variables in Run Scripts
When you create it the Run Script, make sure you add LISTs for the Parameters, to make it easy to run exactly what you want, and not have user error.
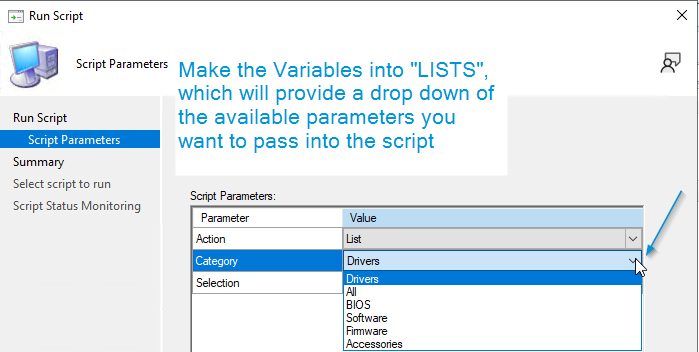
I ran it on a machine I just re-imaged.. it took about 15 minutes.
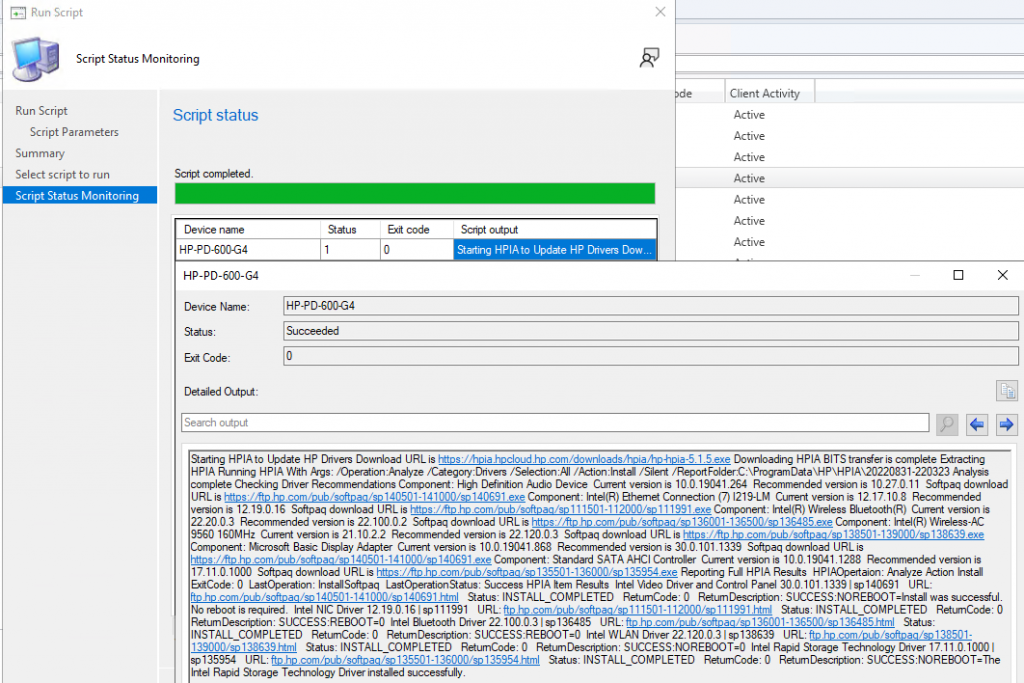
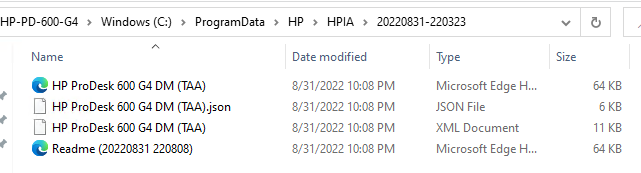
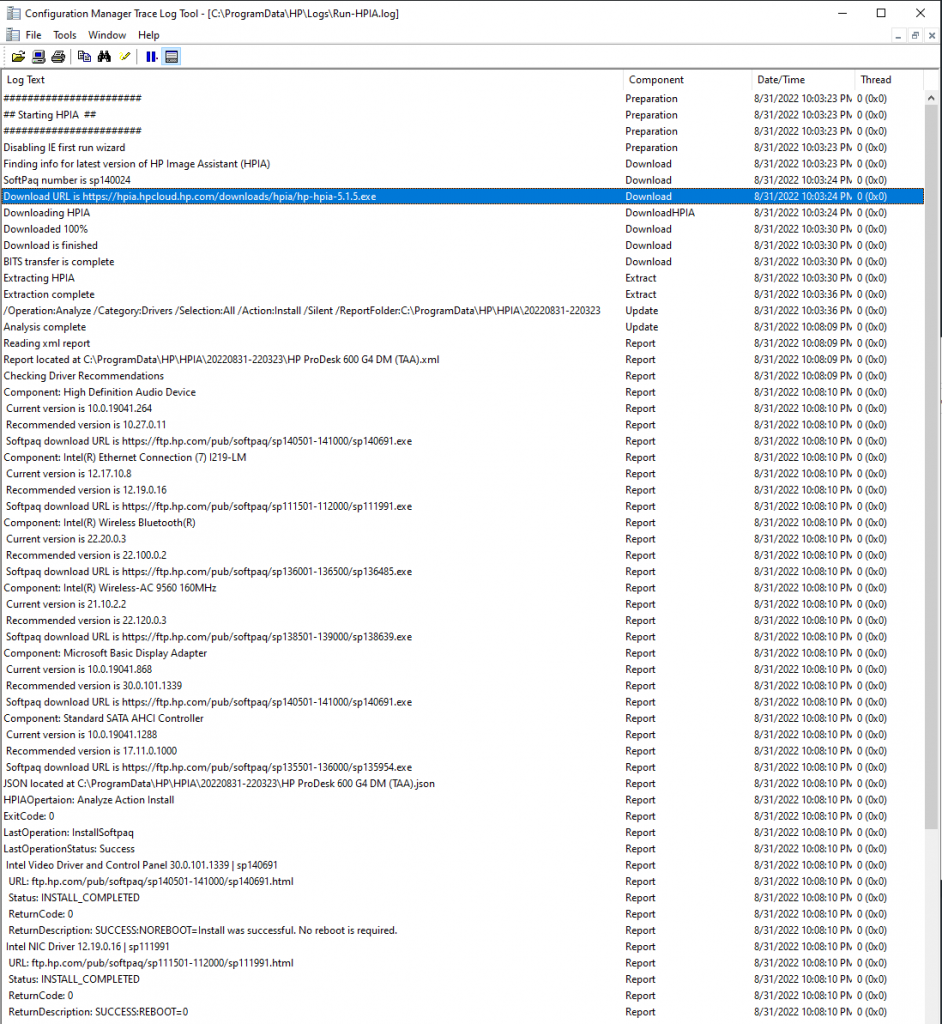
There is a lot of information there, and if you want to see cleaner info, you can always look at the logs on the endpoint.
I also added the ability to have the device restart after you run HPIA, but I’m not going to demo that here.
Posted on GARYTOWN.COM
Hi,
it really seems an awsome script. I’m trying to import it to SCCM. How did you get the selection list for the params required ?
Thank you in advance
https://garytown.com/configmgr-run-scripts-add-list-for-parameters
Thanks a lot.
It was really there … my fault
It worked like a charm
Really appreciate it
Hi, as always a cool idea and a cool script! Thanks!
I added the following parts, in case someone is interested…
Right after the CMTraceLog-function and the “intro” lines:
# Check HP Device
Try {
$Manufacturer = (Get-WmiObject -Class Win32_ComputerSystem).Manufacturer
If (!(($Manufacturer -like “HP*”) -or ($Manufacturer -like “Hewlett-*”))) {
CMTraceLog –Message “Manufacturer not HP. Exit Script.” –Component “Preparation” -Type 3
Write-Host “Manufacturer not HP. Exit script.” -ForegroundColor Red
throw
} Else {
CMTraceLog –Message “Manufacturer HP detected. Continue.” –Component “Preparation” -Type 1
Write-Host “Manufacturer HP detected. Continue.” -ForegroundColor Green
}
}
Catch {
CMTraceLog –Message “Failed to to get Manufacturer. Exit script.” –Component “Preparation” -Type 3
Write-Host “Failed to to get Manufacturer. Exit script.” -ForegroundColor Red
throw
}
# Get latest HPIA Info
# Set proxy settings
$Proxy = “http://proxy.domain.com:Port”
$Username = “user@domain.com”
$Password = ConvertTo-SecureString ‘password’ -AsPlainText -Force
$Credentials = New-Object System.Management.Automation.PSCredential (“$Username”, $Password)
…
$HTML = Invoke-WebRequest –Uri $HPIAWebUrl -Proxy $Proxy -ProxyCredential $Credentials –ErrorAction Stop
## Suspend BitLocker if Category BIOS is selected
If (($Category -eq “BIOS”) -and ($Action -eq “Install”)) {
CMTraceLog -Message “Category $Category and Action $Action selected. Try to suspend BitLocker.” -Component “Preparation” -Type 2
Write-Host “Category $Category and Action $Action selected. Try to suspend BitLocker.” -ForegroundColor Yellow
Try {
$BitLocker = Get-BitLockerVolume -MountPoint c:
CMTraceLog -Message “BitLocker ProtectionStatus is $($BitLocker.ProtectionStatus)” -Component “Preparation” -Type 1
Write-Host “BitLocker ProtectionStatus is $BitLocker” -ForegroundColor Green
Try {
$BitLocker | Suspend-BitLocker -RebootCount 1 | Out-Null
CMTraceLog -Message “Suspended BitLocker RebootCount 1” -Component “Preparation” -Type 1
Write-Host “Suspended BitLocker RebootCount 1” -ForegroundColor Green
} #Try
Catch {
CMTraceLog -Message “Failed to suspend BitLocker. Exit script.” -Component “Preparation” -Type 3
Write-Host “Suspended BitLocker RebootCount 1” -ForegroundColor Red
throw
} #Catch
} #Try
Catch {
CMTraceLog -Message “Failed to get BitLocker ProtectionStatus. Exit script.” -Component “Preparation” -Type 3
Write-Host “Failed to get BitLocker ProtectionStatus. Exit script.” -ForegroundColor Red
} #Catch
} #If
And you can encode your “password.bin” file with base64 and add the following parameter
“/BIOSPwdData:””base64encodedpassword.binstring”””
So you are able to update BIOS with password set.
And
“/ProxyURL:proxy.domain.com”,
“/ProxyPort:proxyport”,
“/ProxyUser:user”,
“/ProxyPassword:password”,
“/ProxyDomain:domain.com”
to use the script behind a proxy.
I hope this helps, too.
Dietmar