I’m pretty good about keeping our Dell machines at the current BIOS level, usually a couple models get updates every month… then there was that Intel AMT vulnerablity, and they released updates for nearly all of our models, so that was fun. I tweeted about my exploits and had requests to share how I’m doing it… so here it is…
App Model & Power Shell
I blogged a 3 part post back in Dec 2015, I’m not going to redo everything, but send you there if you need to build your collections yet:
https://garytown.com/updating-dell-bios-with-configmgrpost-1creating-model-based-collections
Another Pre-Req is having a global condition for “Model”, which I cover here: https://garytown.com/updating-dell-bios-with-configmgrpost-3the-application-deployment
Once you have that out of the way, it’s just building your App.
It’s really simple, we have a PowerShell script that will:
- Suspend Bitlocker (Works for Win 7-10)
- Stop the MBAM Service (So MBAM doesn’t start Bitlocker again before rebooting)
- Grab Dell Bios info from the Bios EXE file in same directory
- Create Log File name based on that EXE
- Confirm Bitlocker is Suspended
- Update Bios, creating Log File
- Reboot Machine
- Reboots right away if no one is logged on
- Give 5 Minute & 2 Minute warnings if someone is logged on
The nice thing about this method, it’s one script, that never changes. You just add it to your Model Folder. Every time a new BIOS comes out, replace the BIOS.EXE in the source, update the Application Detection Method, and update the content for that deployment. All Set!
Now the Script:
There are 2 parameters, you tell it where you want your log file, and what your BIOS password is. That’s it:
<#
.SYNOPSIS
Post-deployment Dell BIOS Updater
.DESCRIPTION
Post-deployment Dell BIOS Updater - Created by Gary Blok @gwblok and Mark Godfrey @Geodesicz
.PARAMETER BIOSpassword
I'll give you two guesses what this parameter is for, and the second one doesn't count
.PARAMETER LogPath
Location to store logging data . . . no not include a slash at the end
.EXAMPLE
BIOSUpdate.ps1 -BIOSPassword G00dP@s$ -LogPath C:\LogCity\BIOS
.LINK
https://www.garytown.com, http://www.tekuits.com
#>
[CmdletBinding()]
Param(
[Parameter(Mandatory=$true,Position=1,HelpMessage="BIOS Password")]
[ValidateNotNullOrEmpty()]
[string]$BIOSpassword,
[Parameter(Mandatory=$true,Position=2,HelpMessage="Log Path")]
[ValidateNotNullOrEmpty()]
[string]$LogPath
)
#Get Bios File Name (Uses the Bios EXE file in the same folder)
$BiosFileName = (Get-ChildItem *.exe).Name
#Get Bios File Name (No Extension, used to create Log File)
$BiosLogFileName = (Get-ChildItem *.exe).BaseName + ".log"
#Create Variable of Bitlocker Status
$Volume = Get-WmiObject -Namespace root\cimv2\security\microsoftvolumeencryption -Query "select * from win32_encryptablevolume where DriveLetter = 'C:'"
$Status = $Volume.GetProtectionStatus()
$BitLockerStatus = $status.ProtectionStatus
#Set Arguments for Bios Update
$BiosArguments = "/s /p=$BiosPassword /l=$LogPath\$BiosLogFileName"
#Check if User is Logged In
$Session = (Get-WmiObject win32_computersystem).UserName
#Check if Bilocker enabled, then suspened.
If ($BitlockerStatus -eq '1'){$Volume.DisableKeyProtectors()}
$Status = $Volume.GetProtectionStatus()
$BitLockerStatus = $status.ProtectionStatus
If($BitLockerStatus -eq '1'){
mofcomp.exe c:\windows\system32\wbem\win32_encryptablevolume.mof
Manage-bde.exe -protectors -disable c:
}
#Update Variable of Bitlocker Status
$BitLockerStatus = $status.ProtectionStatus
#Stop MBAM Agent, to prevent autoresume of Bitlocker:
Stop-Service -Name MBAMAgent -Force
#If Bitlocker suspeneded, Update Bios
If ($BitlockerStatus -ne '1'){
$Process = Start-Process "$PSScriptRoot\$BiosFileName" $BiosArguments -Wait -PassThru
#Start-Sleep -s 30
}
If($Process -ne $null -and $Process.ExitCode -eq '2'){
# User is Logged In, Give 5 minute warning, if not, reboot in 5 seconds.
If ($Session -ne $null){
Start-Process shutdown.exe -ArgumentList '/r /f /t 300 /c "Updating Bios, please save your work, Computer will reboot in 5 minutes"'
}
else{Start-Process shutdown.exe -ArgumentList '/r /f /t 5 /c "Updating Bios, Computer will reboot in 5 seconds"'
}
}
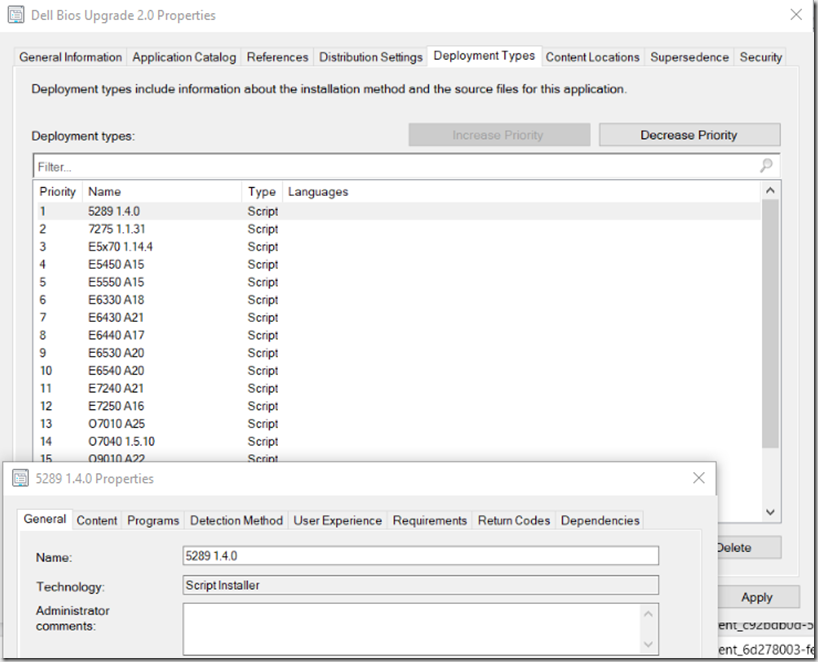
Deployment Types, One Per Model, this will make the download quick, as it only downloads the one for that model, and gives you the ability to do easy detection rules.
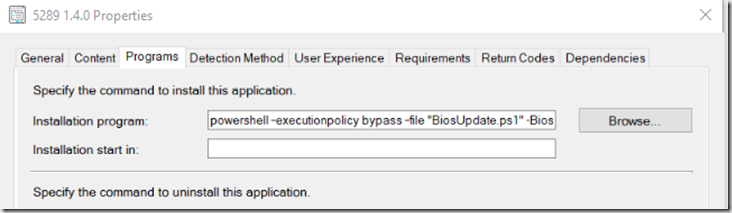
Programs: powershell –executionpolicy bypass –file “BiosUpdate.ps1” –Biospassword P@ssw0rd -LogPath C:\Cabs\InstallLogs
– Change your Bios Password & where you want to save the log files.
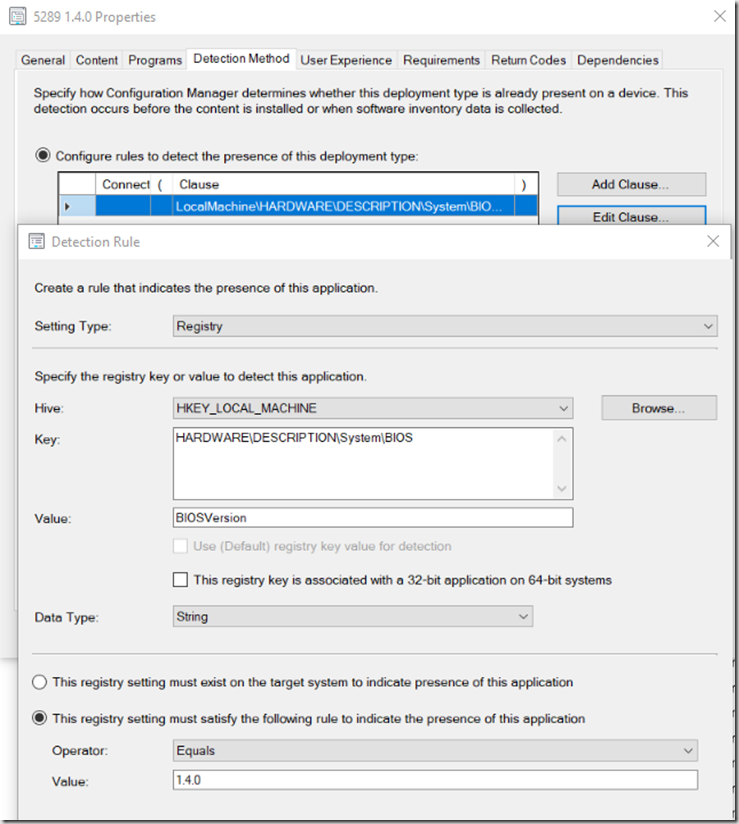
Detection is just a Registry Key:
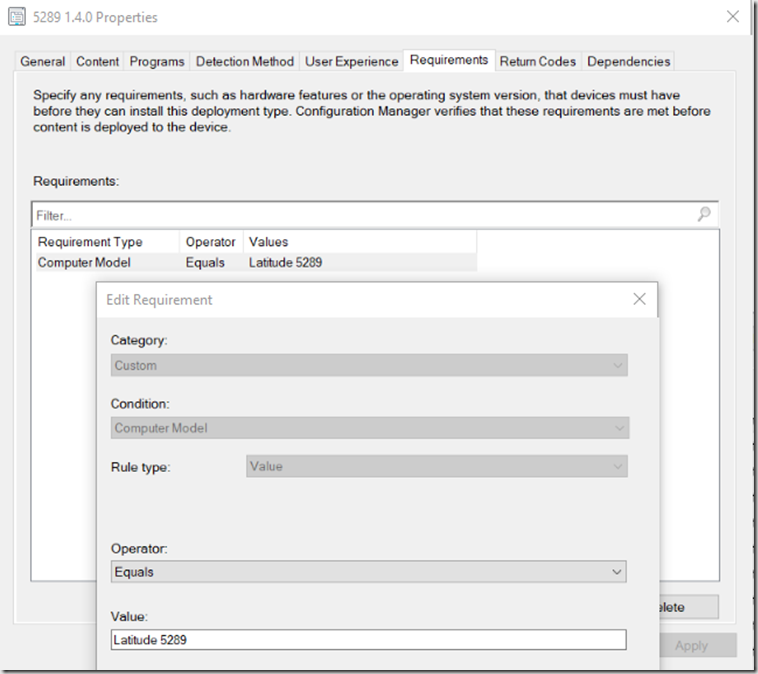
Requirements: Model = the Model (see previous post for more details)
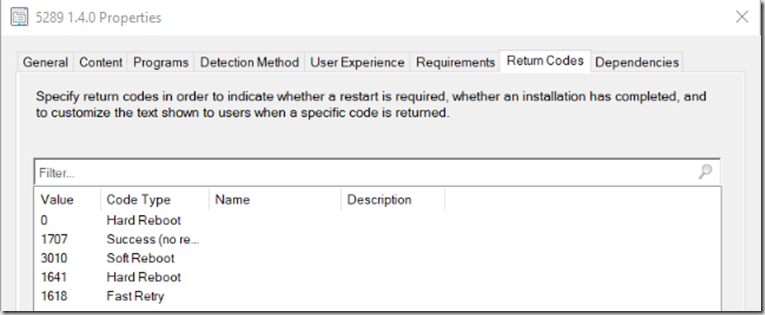
Return Code, Change 0 = Hard Reboot
Actual Content for Deployment Type:
Contains the PowerShell File (Which you don’t need to change, works for every model & every version of the Bios)
There you have it, for your deployments
Download AppExport & Script HERE. If you choose to import the App, you’ll want to build your own Folder Structure and update the Content Tab for each deployment.
Leave a comment if you have a question, or hit me up on Twitter – @gwblok
Gary — How do you handle different BIOS passwords? We have many Dell models and they could have any one of 3 different passwords we have used to secure the BIOS over the years. I’d like to be able to update the BIOS AND change the password to a standard password for all systems at the same time. Can the script do that?
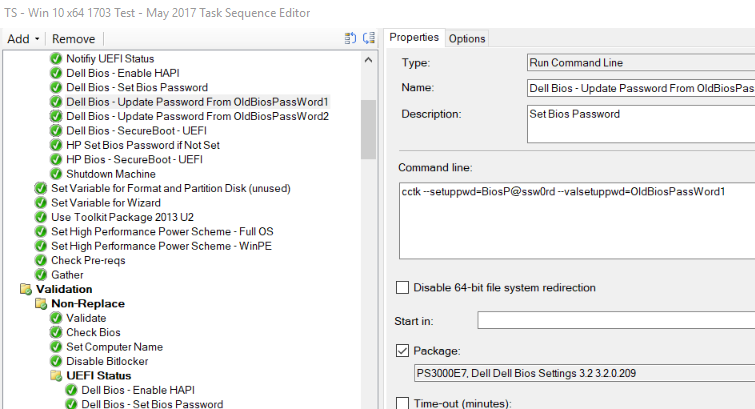
Bios Passwords: You’d create as many steps as needed (set continue on error), but basically 1 step to set password if not set, then each additional step to set the password to your new password, using the list of old passwords
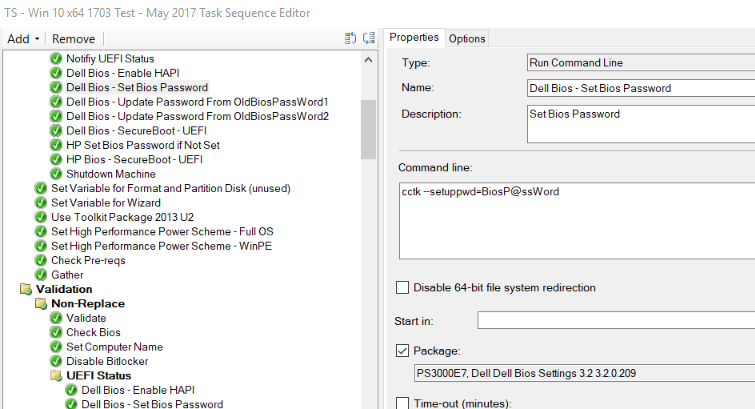
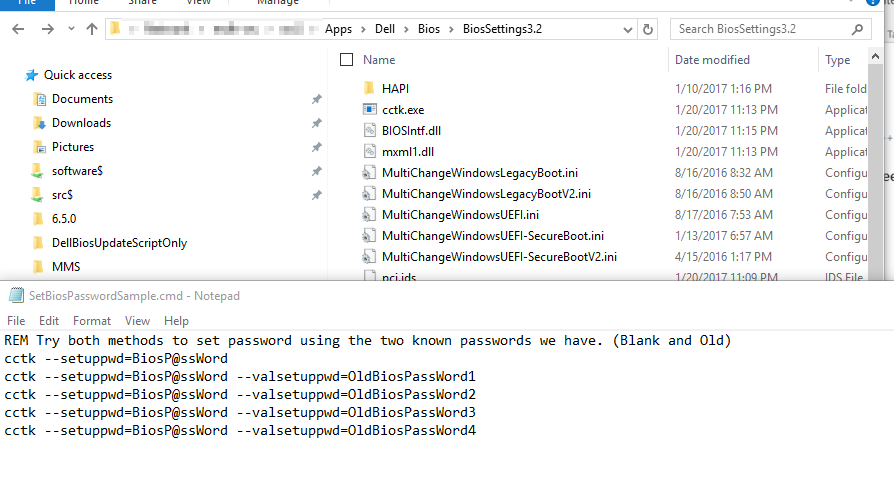
Set Bios Password if Blank: cctk –setuppwd=BiosP@ssWord
Update Bios Password: cctk –setuppwd=BiosP@ssWord –valsetuppwd=OldBiosPassWord
Or you can use a script to push to all Machines Post OSD.
good stuff! I’ve been asked many times to do the same. we have over 10K endpoints of over 170 different models. would need a FTE to manage. question, I have issues with the detection method biosversion equals 1.4.1 (as an example). some newer bios versions use a different format (i.e. 1.04.01). so obviously we know that 1.4.1 is greater than 1.04.01, but sccm doesn’t think so. ever encountered this?
HI Gary
We implemented your solution in SCCM 2012 R2 and works perfect thanks for that
Now we busy with migrating our environment to SCCM CB 1802 we encounter some problems with this solution , does this solution of yours still works in SCCM CB 1802
Regards
Johan
I don’t know why it wouldn’t still work, but I changed companies and no longer am responsible for BIOS updates and have not used this process in over a year. If you find any info about your issue, please post it here.
You can use ReleaseDate, I saw someone mention using that before rather than version.
Apologies also another query, the reboot prompt doesn’t seem to function on any of the Windows 7 machines I have tested so far…
I know I used to run it on win 7 and 8 and it gave prompts for the reboot. I haven’t used this in over a year since I switched jobs and no longer have this responsibility, and I don’t have the ability to test this at home. It should work, perhaps update WMF on one of your test machines and try again.
No problem – thanks for the response Gary. I will let you know how I get on
Okay so just to update you, my original statement wasn’t giving you the clear picture – the issue I was having was the actual BIOS install wasn’t going ahead. On testing the commands, Windows 7 machines didn’t like the $PSScriptRoot variable, which didn’t exist until PowerShell 3.0, so I have amended the script and added a if statement in to set the variable manually.
So I think your original statement of updating WMF would still have been valid and fixed this.
Hi Gary,
Thank you for sharing your method, I have just updated my precision 5510 BIOS successfully using your script/collections but I am using the Software Center (like a normal application) and the status is “Failed”.
Also I am hesitant deploying the script as “required” since you will force a restart on users, and I am how do you go in communicating this to users? I do not want my CEO to get a system restart while she is in the middle of a meeting.
Cheers,
Thomas
Couple questions on the script in this post (I know it is a bit dated, so you may have moved on in life :)). . .
1. Why are you executing mofcomp.exe c:\windows\system32\wbem\win32_encryptablevolume.mof?
2. How do you handle re-enabling bitlocker on Windows 7 systems? I don’t believe it re-enables automatically after a reboot?
Thanks,
Jeff
Looking at the script, I’m not seeing anything that would stop this from utilizing HP or Lenovo’s. Haven’t looked at their BIOS files to see if they are .exe files or not, but would this work?
Same process should work for HP and Lenovo. I did this with HP as well back in the day, so I know that works. You’ll have to switch out the command lines for running the Bios upgrades, but yes, it should work fine.
I’ve found that (Get-WmiObject win32_computersystem).UserName behaves differently on Win7 -> Win10.
So I parse quser to check active console or RDP user sessions:
$LoggedinUserData = (((quser) -replace ‘\s{2,}’, ‘,’ | convertfrom-csv ) | ? {($_.sessionname -match ‘console’) -and ($_.state -eq ‘Active’)})
If ($LoggedinUserData -eq $null)
{
$LoggedinUser = (((quser) -replace ‘\s{2,}’, ‘,’ | convertfrom-csv ) | ? {($_.sessionname -match ‘RDP’) -and ($_.state -eq ‘Active’)}).USERNAME.Replace(‘>’,”)
}
Else
{
$LoggedinUser = $LoggedinUserData.USERNAME.Replace(‘>’,”)
}
A great process only thing I would say is that the pop that the user recieves is not set in focus hence the machine usually reboots even without them knowing. Is there a way to great a dialog box that shows the restart is about to happen with a countdown ?
Leverage PowerShell App Deploy Toolkit or Move to a Task Sequence.