First off, I want to give credit where Due, I first borrowed this idea from Jeremy @ syswow
– http://syswow.blogspot.com/2012/05/secure-dod-drive-wiping-with-sccm.html
Then Modified it to give feed back to our Service Desk, and keep a record on the Server
Also changed it from one 1 step to run 7 passes, to having 7 steps run a single pass, so when you look at the TS Progress, you know what pass it is on.
Look back to his blog for more details, as he explains the sdelete command and parameters used.
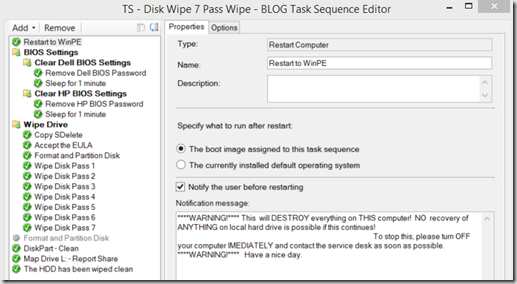
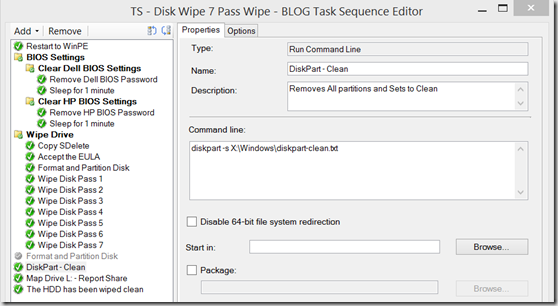
Overview of TS
- Restart to WinPE (x86)
- Bios Settings – We have it clear our Bios Password, since they machines will be going recycle
- Wipe Drive Section
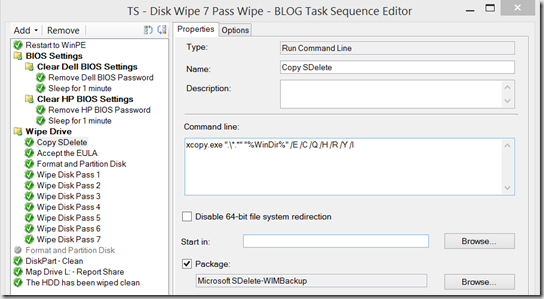
- Copy SDELETE – Copies the Files the “OS” to be used (sdelete.reg, diskpart-clean.txt, and batch file used at end)
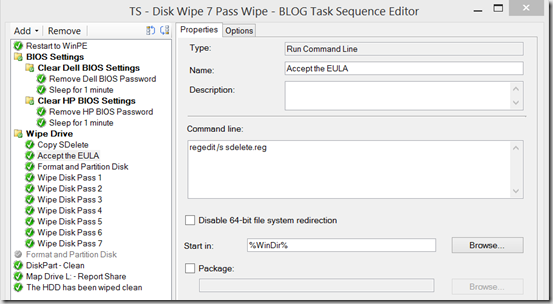
Run Command Line – xcopy.exe “.\*.*” “%WinDir%” /E /C /Q /H /R /Y /I - Accept the EULA – adds registry key to OS Registry
regedit /s sdelete.reg
Start in: %WinDir% - Format and Partition Disk – Runs a TS format Step
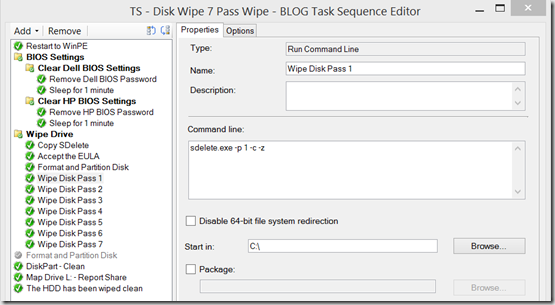
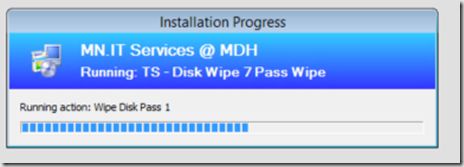
- 7-13 – Runs a Pass of sdelete (Running 7 separate passes so you can label each pass, so the someone watching knows what pass they are on)
Run Command Line – sdelete.exe -p 1 -c -z - Diskpart – Clean – Removes any Paritions and leaves the drive a blank
Run Command Line – diskpart -s X:\Windows\diskpart-clean.txt - Map Drive L: – Report Share – This maps a Drive, granting access for the Next Step to save a file on the Network
Run Command Line – net use l: \\server.fqdn\share$\DiskWipeResults /user:domain\username password - Posts information once Wipe is completed, and saves logs on the Servers
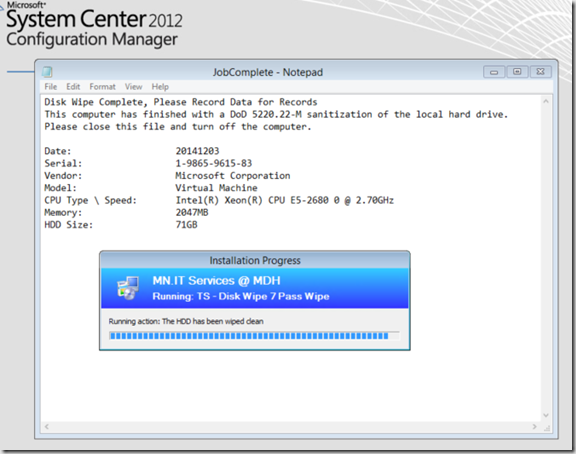
Run Command Line – x:\Windows\JobComplete.bat
2 Logs are Modified. It first will create a log for the indivdual machine, which can be printed and attached to the machine
It then appends to a log showing all computers that have undergone this process
Screen Captures:
Step Format and Partition Disk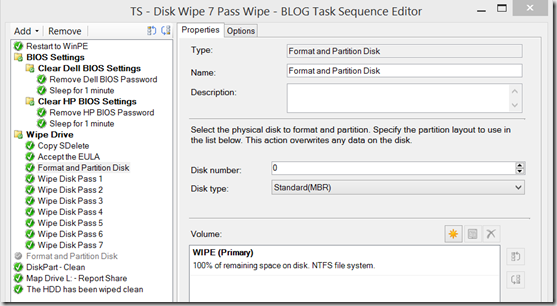
Step: Map Drive l: (requires an account with permissions to the share specified. Recommend a Service Account that is locked down to only that share, and does not have logon rights)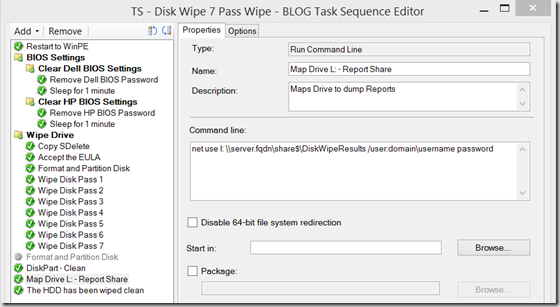
Step: The HDD has been Wiped Clean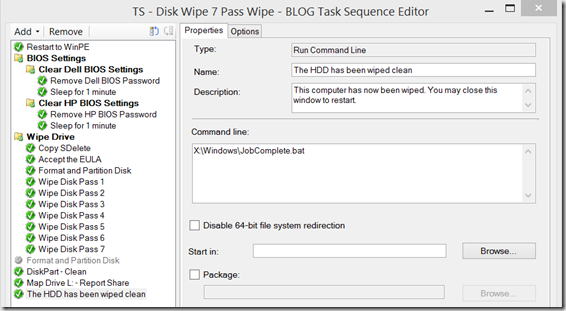
Capture of Process:
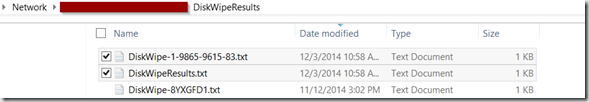
Logs on Server:
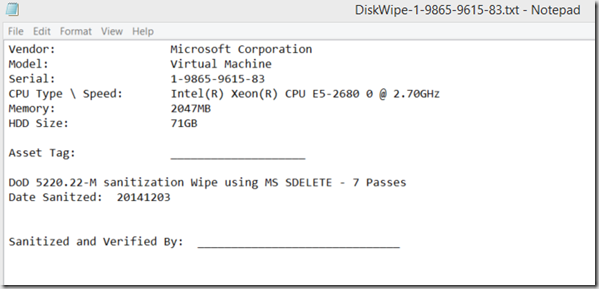
Creates a DiskWipe-SERIAL.txt file & Appends to the DiskWipeResults.txt file.
DiskWipeResults.txt:
It will then append the next computer, and so on to keep a running log of all.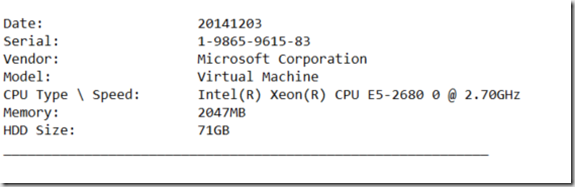
Files Needed: (Also available in LINK at bottom)
JobComplete.bat file:
——
Echo off
for /F “skip=2 tokens=2 delims=,” %%A in (‘wmic systemenclosure get serialnumber /FORMAT:csv’) do (set “serial=%%A”)
set serial=%serial:~-15%
for /F “skip=2 tokens=2 delims=,” %%A in (‘wmic csproduct get vendor /FORMAT:csv’) do (set “compvendor=%%A”)
for /F “skip=2 tokens=2 delims=,” %%A in (‘wmic csproduct get name /FORMAT:csv’) do (set “compname=%%A”)
for /F “skip=2 tokens=2 delims=,” %%A in (‘wmic CPU get name /FORMAT:csv’) do (set “CPUname=%%A”)
for /F “skip=2 tokens=2 delims=,” %%A in (‘wmic computersystem get totalphysicalmemory /FORMAT:csv’) do (set “memory=%%A”)
set /a memory = memory / 1048576
for /F “skip=2 tokens=2 delims=,” %%A in (‘wmic diskdrive get size /FORMAT:csv’) do (set “hddsize=%%A”)
set hdd=%hddsize:~0,-4%
set /a hdd=hdd/1048576
set TimeStamp=%DATE:~10,4%%DATE:~4,2%%DATE:~7,2%
REM Creates Network Log File
echo. >>l:\DiskWipeResults.txt
echo Date: %TimeStamp% >>l:\DiskWipeResults.txt
echo Serial: %serial% >>l:\DiskWipeResults.txt
echo Vendor: %compvendor% >>l:\DiskWipeResults.txt
echo Model: %compname% >>l:\DiskWipeResults.txt
echo CPU Type \ Speed: %CPUname% >>l:\DiskWipeResults.txt
echo Memory: %Memory%MB >>l:\DiskWipeResults.txt
echo HDD Size: %hdd%GB >>l:\DiskWipeResults.txt
echo ____________________________________________________________ >>l:\DiskWipeResults.txt
REM Creates Network Label for Machine
echo Vendor: %compvendor% >>l:\DiskWipe-%serial%.txt
echo Model: %compname% >>l:\DiskWipe-%serial%.txt
echo Serial: %serial% >>l:\DiskWipe-%serial%.txt
echo CPU Type \ Speed: %CPUname% >>l:\DiskWipe-%serial%.txt
echo Memory: %Memory%MB >>l:\DiskWipe-%serial%.txt
echo HDD Size: %hdd%GB >>l:\DiskWipe-%serial%.txt
echo. >>l:\DiskWipe-%serial%.txt
echo Asset Tag: ____________________ >>l:\DiskWipe-%serial%.txt
echo. >>l:\DiskWipe-%serial%.txt
echo DoD 5220.22-M sanitization Wipe using MS SDELETE – 7 Passes >>l:\DiskWipe-%serial%.txt
echo Date Sanitzed: %TimeStamp% >>l:\DiskWipe-%serial%.txt
echo. >>l:\DiskWipe-%serial%.txt
echo. >>l:\DiskWipe-%serial%.txt
echo Sanitized and Verified By: ______________________________ >>l:\DiskWipe-%serial%.txt
REM Creates Local Log file that displays at end of Process
echo Disk Wipe Complete, Please Record Data for Records >>X:\Windows\JobComplete.txt
echo This computer has finished with a DoD 5220.22-M sanitization of the local hard drive. >>X:\Windows\JobComplete.txt
echo Please close this file and turn off the computer. >>X:\Windows\JobComplete.txt
echo. >>X:\Windows\JobComplete.txt
echo Date: %TimeStamp% >>X:\Windows\JobComplete.txt
echo Serial: %serial% >>X:\Windows\JobComplete.txt
echo Vendor: %compvendor% >>X:\Windows\JobComplete.txt
echo Model: %compname% >>X:\Windows\JobComplete.txt
echo CPU Type \ Speed: %CPUname% >>X:\Windows\JobComplete.txt
echo Memory: %Memory%MB >>X:\Windows\JobComplete.txt
echo HDD Size: %hdd%GB >>X:\Windows\JobComplete.txt
X:\Windows\JobComplete.txt
——-
sdelete.reg file:
——-
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Sysinternals\SDelete]
“EulaAccepted”=dword:00000001
——–
Package Contents (Scripts and Files used): http://garytown.com/Downloads/SDelete.zip
Sdelete download: http://technet.microsoft.com/en-us/sysinternals/bb897443.aspx
Great article – needs one change to work in CONFIGMGR R2 Sp1 and greater.
SDelete -p C: -c -s -z /AcceptEULA
I’m currently running ConfigMgr R2 SP1, with Window 10 x86 WinPE, and it is working without adding the /AcceptEULA. The Step to accept EULA takes care of it. I’m running the TS right now to confirm that it is working… on Wipe Disk Pass 1, might be awhile before it finishes. But so far so good.
Thx, great article.
I’ve added a JobStart.bat to write startdate and starttime to txt files and in JobComplete read starttime to compare the white duration. Also I’ve added mic csproduct get version (lenovo device names are in version).
Br
Pat
I had to change the SDelete command to:
sdelete64.exe -p 1 -c C: -z
It was requiring a drive letter to work.
Did you have the “Start in” part set to c:\?
I had the same issue, fixed in the same way and yes the “Start in” part was set to c:\
Yessir. Also, it appears there is a bug with SDelete 2.0 where it takes much longer/hangs at 100% and folks are recommending to use 1.61.
https://forum.sysinternals.com/sdelete-hangs-at-100_topic32267.html
Thanks again for this article! It was quite helpful!
Thanks, I appreciate the information. I haven’t used this method since we went with Active Killdisk. (Business Requirement, I can’t say it’s actually any better, it’s definitely more complicated).
Hi Guys, can any one give me a indication as to how long this process took to complete? I am using SDelete.exe 1.61 and it has been running for 4 hours now, still on Pass 2
It can take awhile depending on Computer hardware, size of drive, etc. It typically takes several hours with good hardware & SSDs. One think you can do is add the PowerCFG.exe command to make sure it’s using High Performance Mode utilizing that CPU to make 1s and 0s as fast as it can. – https://blogs.technet.microsoft.com/deploymentguys/2015/03/26/reducing-windows-deployment-time-using-power-management/
Do you happen to know if there’s any documentation for SDelete and whether it properly can wipe an SSD?
I believe it can properly wipe an SSD, however I haven’t found anything official. I did test on SSDs quite a lot, but I never had them verified with ontrack, etc.
Some useful Links:
https://www.kennethghartman.com/securely-delete-files-with-sdelete/ (CISSP guy who recommends it)
https://technet.microsoft.com/en-us/library/2009.08.utilityspotlight.aspx
Official Docs: https://docs.microsoft.com/en-us/sysinternals/downloads/sdelete
Tis command is sdelete64.exe -p 1 -c C: -z, trying on my hyper-v Gen 2 machine.
Hello Gwblok,
Great guide for wiping!
What commands did you use for clearing HP Bios password?
Many thanks,
I forget off hand, it’s in the HP Docs. Basically you’re just setting a password of blank. If I was re-writing today, I’d probably leverage HPCMSL, but watch https://miketerrill.net/, I know he has been working. You do need to know the current password to be able to remove the password.
Doesn’t work, I get this error immediately after booting into winpe:
“The task sequence execution engine failed execution of a task sequence. The operating system reported error 2147942403: The system cannot find the path specified.”
I guess this was the first step of the sdelete copy command, it does not have much more detail from the alerts.
Typically if it can’t find the path, it can’t find the path to the file you’re calling, sdelete.
Follow standard troubleshooting methods at this point, Add a Pause and see if you can run the command manually.
Does anyone know if this article is still valid with the current SCCM build. I am on version 2010. I have the task sequence created, and it goes to the formatting of the drive, and then when it goes to do the SDelete part, it errors out.
Any assistance would be greatly appreciated.
Thank you.
You’ll need to confirm that you’re formatting the drive before hand. If you have more details on the error message, that would be helpful. Typically the SMSTS.log would provide the clues needed.
Hi sir,
Just a bit confused about Runs a Pass of sdelete steps. Do I run same command in each step or I need to change the number as per below:
sdelete.exe -p 1 -c -z
sdelete.exe -p 2 -c -z
sdelete.exe -p 3 -c -z
.
.
it runs 7 single passes, the reason is because to be considered a secure wipe, it needed to run 7 times, but I didn’t want to have 1 step run the pass 7 times, I wanted to have 7 steps each run one pass so if someone was watching, or it failed, it would be easy to see how many wipes have already run.
Hi!
your guide is amazing, thanks a lot. But i have a question: When sdelete is done wiped then can continue to installation windows 10? MDT is stuck after wiped and wont continue next task sequence.
I haven’t tested this in MDT, I know what you’re asking is possible in ConfigMgr.
Very good guide.
Just wondering if it has been tested in MDT, since?
I am trying to get something to work, in MDT, which will do a deep wipe.
I don’t do any testing in MDT, but sdelete would work fine in any WinPE environment, so you should be able to use this as your guide to rebuild in MDT.