This will grab the Machine Password Change Date from the local machine. It MUST be run as system to access the required registry keys. If you’re using Config Mgr, and you use this in a Package / Task Sequence, it runs as system, so you’re good to go. If you’re testing, you can use this little trick: Run PowerShell ISE as System to Test scripts… From Software Center
Code:
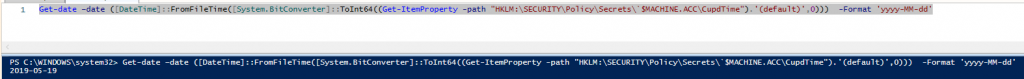
Get-date –date ([DateTime]::FromFileTime([System.BitConverter]::ToInt64((Get-ItemProperty -path "HKLM:\SECURITY\Policy\Secrets\`$MACHINE.ACC\CupdTime").'(default)',0))) -Format 'yyyy-MM-dd'
Thanks to this Post that helped me find the registry Key. This script is much more in-depth and works if you don’t have SYSTEM access.
Retrieve Time Machine Password Last Reset via PowerShell
So Gary, why did you want to know that information? When you need to revert back to previous build, if you revert back to a time that had an old Machine Account Password in AD, you’ve lost your Domain Trust… ANNOYING! Example. You know your domain policy for how often your machine account changes it’s password is like 30 days, and the last time it changed as 3 days ago. You upgrade your Windows 10 machine to the latest build, about 5 days later (2 days after the Machine Account Password in AD changed), you realize a business critical app doesn’t work, so you run the OS Uninstall (Go back..) Process, it reverts the machine and the machine now has the old password, and the domain has the new password, and you lost your trust relationship.
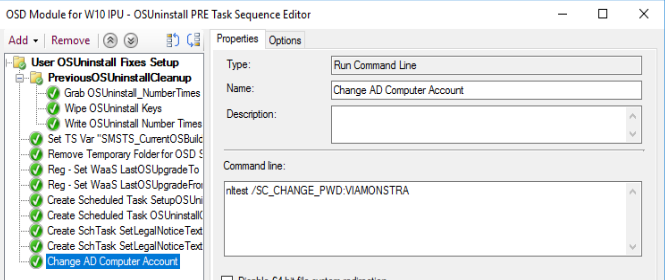
Solution, force a change of the password during the upgrade process.
Code:
nltest /SC_CHANGE_PWD:DOMAINNAME
So basically the code that provides that last change date is to make sure that if I revert to previous build, I don’t loose my domain trust.
GARYTOWN.COM
Comments are closed.