Required Reading: KB5025885: How to manage the Windows Boot Manager revocations for Secure Boot changes associated with CVE-2023-24932 – Microsoft Support
Related:
- KB5025885 – Updating your USB Boot Media – Leveraging OSD Module
- ConfigMgr Task Sequence – KB5025885: How to manage the Windows Boot Manager revocations for Secure Boot changes associated with CVE-2023-24932
Words of Warning
Once you’ve applied the mitigations outlined in the KB, the device is difficult to work with when it comes to boot media / reimaging. Personally, I’d only do this on some lab test machines, and not rollout to larger groups until MS provides a better story for managing post mitigated machines. My assumption is that this will be a horror story until October when 24H2 is released.
My Thoughts, take it or leave it…
Get a couple test devices and apply all 3 steps. Learn the pain firsthand! Get a few more test devices and only apply steps 1 & 2. I’ve updated my TS to only do steps 1 & 2 for now.
After some testing, start to roll out Steps 1 & 2 (NOT 3) to a broader scope of devices. Since it takes so many reboots (if you don’t push with a TS), you can let these changes slowly filter out as end users naturally reboot. Recommend #ConfigMgr Baseline / #Intune Remediation
When (if) MS releases 24H2 ADK (Hopefully July based on the KB), start updating your boot media and continue testing on the couple devices you have applied all 3 steps on.
Then for Step 3 wide deployment, wait for MS to ensure PXE is working, and you have your Windows Media Updated & your Boot Images all updated, and everything is working smoothly on your few test devices, then slowly rollout step 3 to rest of your devices.
On to the Post
TLDR: Scripts on GitHub, Prefix: KB5025885: garytown/ConfigMgr/Baselines/CVE-2023-24932
This script checks the 3 different steps of the remediation process, then applies the appropriate step needed.
It will finally be considered compliant once all 3 steps return “TRUE”, which takes quite a few reboots. Let’s break down the script:
The Script
Applicability
This will ensure that the device has at least the April Patches installed on the device and only run rest of the script if it does.
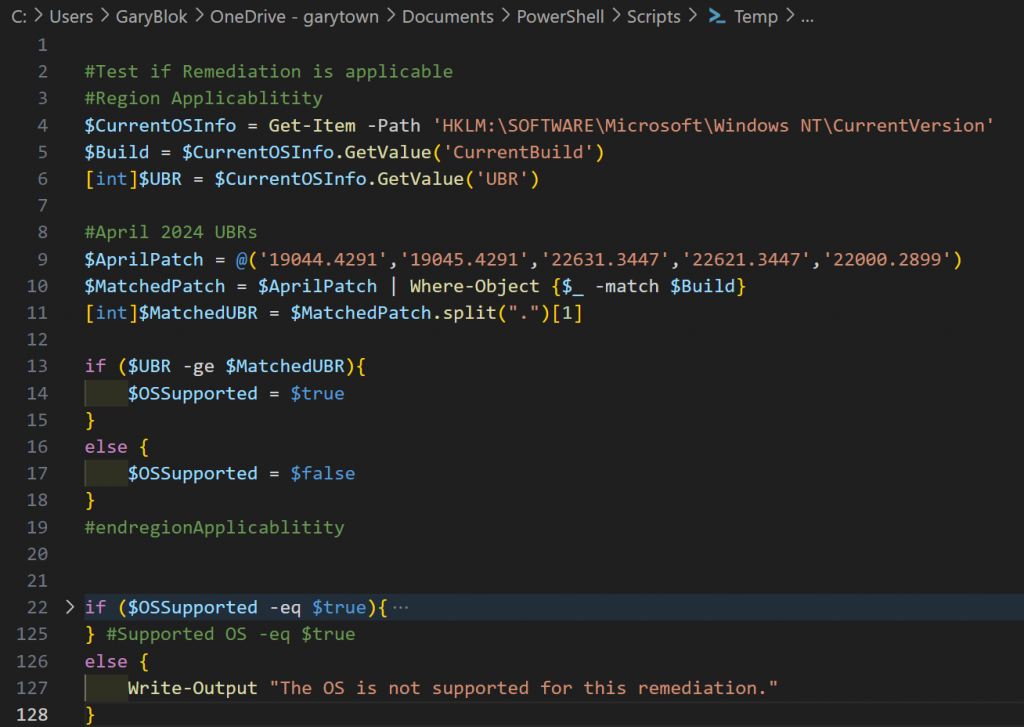
HPCMSL Check (HPCMSL Script only)
This section checks if you have HPCMSL installed, if it doesn’t it enables the reboot notifications. Update the $ToastBase64Image code to your own logo. Update the $param info to what fits for you.
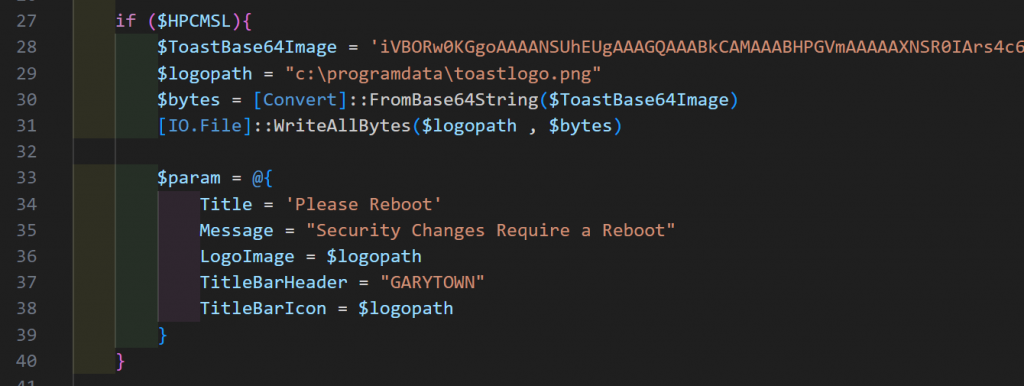
Setup and Step Test
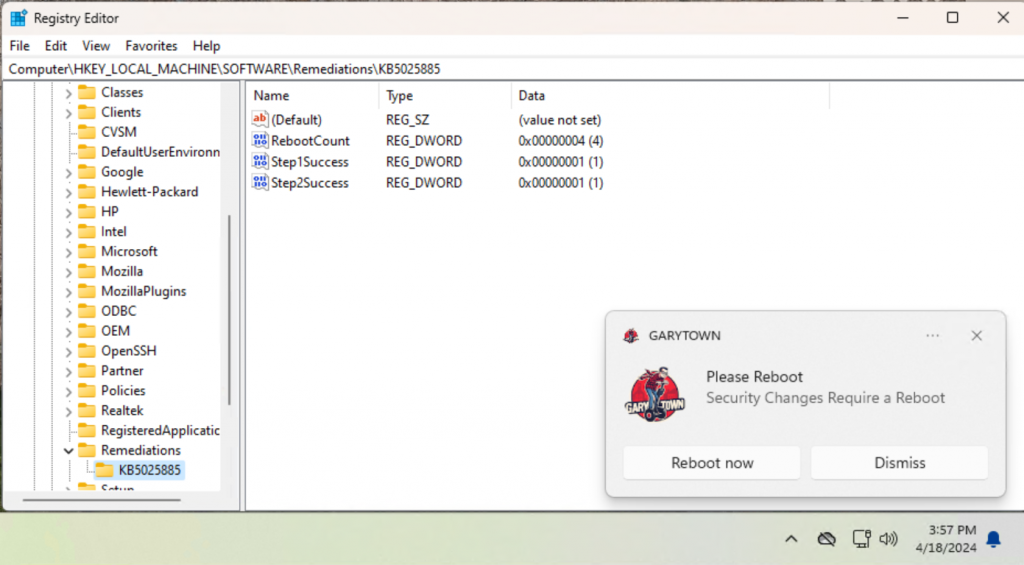
This section sets the registry locations needed, set the initial reboot count to 0, and then does each step test, to determine if it has already been completed or not.
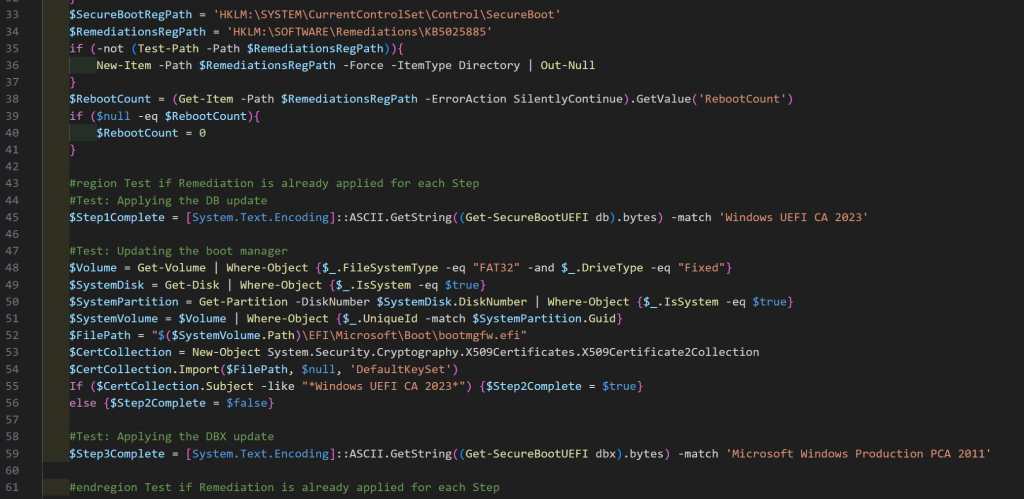
Remediations
Based on the results of the tests, it will find the correct section and apply the needed change, then prompt a toast to reboot (HPCMSL version only).. otherwise you just wait for them to reboot on their own.
In Action
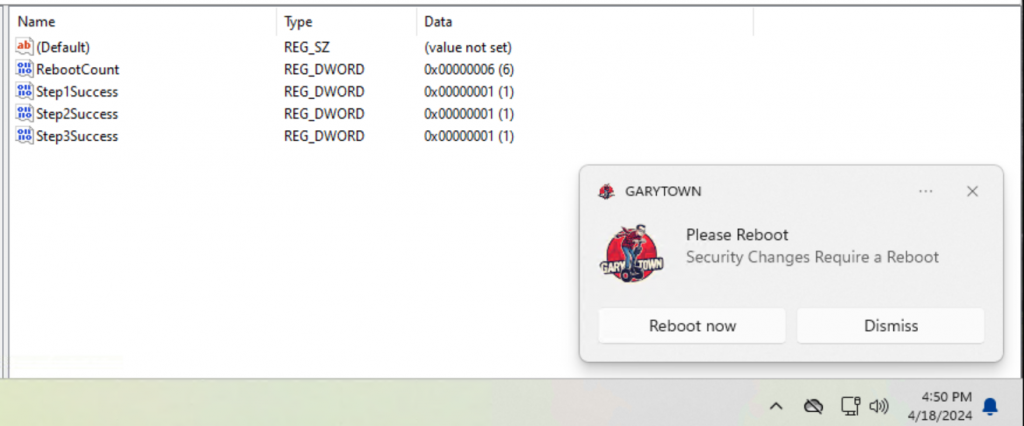
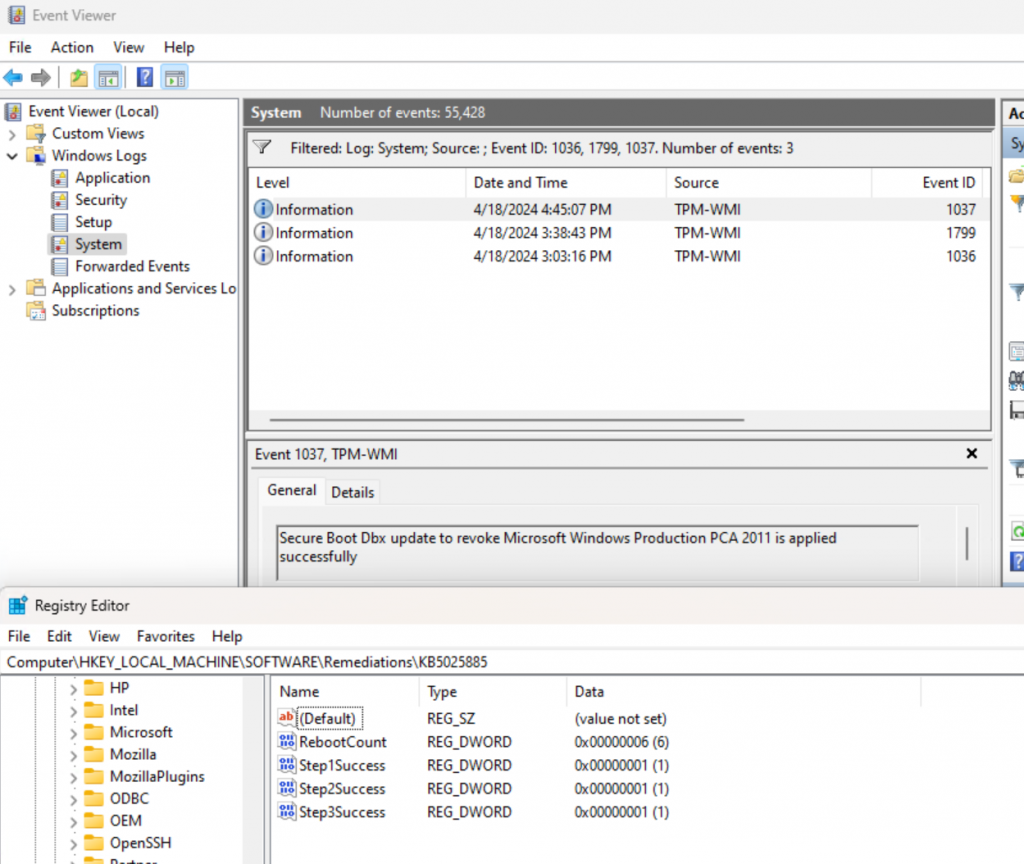
On this device, I’ve triggered the remediation script several times, so it’s already rebooted 4 times, and boths Steps 1 & 2 are confirmed compliant. After the next reboot (number 5), and the next time remediation script runs, it will apply the final step remediation. It will then take one additional reboot (number 6) to come into full compliance. Once in full compliance, it will no longer run the script, as the detection script will report Success on all 3 Steps.
Things to Note
The remediation script has the potential to run several times between reboots. If you have the HPCMSL version launching notifications, end users will be prompted to reboot each time, which is good, it will get the remediations in place. Otherwise, without prompts, this could take months for end users to have 6 reboots!
If the script re-runs, its not a big deal, it will just set the registry values again… and again… until it reboots and moves onto the next stage.
Testing, please test! I’ve done minimal testing. I provide NO support / warranty, etc.
To test faster, just run the script manually, reboot, run, reboot… etc.
Hi Gary !
Would the HPCMSL notifications work on a DELL computer or this is only for HP devices ?
Thanks
Works on a dell too, as long as you deployed the PowerShell Module (HPCMSL) to it.
So I could just use the PS script as a computer startup script and it’ll run everytime the computer boots up and just goes one step further each reboot?
Would that work?
Yes, that should work.
I know that this script needs to be updated as MS changed the process, I just haven’t had time to go back and do that yet.
Good to know, thank you!
Does the script that only applies the first two steps also need to get updated?
Windows 11 24H2 has been released and bootmgr.efi still is signed with the 2011 certificate…
I have also check the latest source files from ms. For exampe 24h2 (each version) and 23h2.
They didnt change anything on the certificate!
And there is still no instruction and support for changing PXE Boot Images in a config manager environment.
What a mess.
I think Microsoft is also unsure about the rollout process worldwide and the vendors too.
Regards