Required Reading: KB5025885: How to manage the Windows Boot Manager revocations for Secure Boot changes associated with CVE-2023-24932 – Microsoft Support
Words of Warning
Once you’ve applied the mitigations outlined in the KB, the device is difficult to work with when it comes to boot media / reimaging. Personally, I’d only do this on some lab test machines, and not rollout to larger groups until MS provides a better story for managing post mitigated machines. My assumption is that this will be a horror story until October when 24H2 is released.
My Thoughts, take it or leave it…
Get a couple test devices and apply all 3 steps. Learn the pain firsthand! Get a few more test devices and only apply steps 1 & 2. I’ve updated my TS to only do steps 1 & 2 for now.
After some testing, start to roll out Steps 1 & 2 (NOT 3) to a broader scope of devices. Since it takes so many reboots (if you don’t push with a TS), you can let these changes slowly filter out as end users naturally reboot. Recommend #ConfigMgr Baseline / #Intune Remediation
When (if) MS releases 24H2 ADK (Hopefully July based on the KB), start updating your boot media and continue testing on the couple devices you have applied all 3 steps on.
Then for Step 3 wide deployment, wait for MS to ensure PXE is working, and you have your Windows Media Updated & your Boot Images all updated, and everything is working smoothly on your few test devices, then slowly rollout step 3 to rest of your devices.
On to the Post
Related Content:
- KB5025885 – Updating your USB Boot Media – Leveraging OSD Module
- PowerShell Script – KB5025885: How to manage the Windows Boot Manager revocations for Secure Boot changes associated with CVE-2023-24932
This is what I came up with in my lab for applying the remediations. I’ve had 2 successful tests so far, 1 VM and 1 Physical HP device. So please TEST TEST TEST!!!!
I’m uploading it now so people can mess with it and hopefully it might save them a little time.
UPDATED Download: KB5025885 Remediation TS - 4 Steps - Panu Update (6566 downloads ) – Version 24.8.29.1 – Panu Saukko updated Version. Includes additional steps that were added in July.
Download: KB5025885 Remediation TS (9356 downloads ) – Version 24.1.17.1 Released (2nd Release) – FULL 3 Step Version
Download: KB5025885 Remediation PART 1 & 2 TS (9669 downloads ) – Version 24.1.19.1 Released – Steps 1 & 2 Only Version
Update 24.1.17.1 – Changes to TS based on feedback from Mike Terrill – Modified checks and flattened groups and added updated conditions.
I’m not going to go over it now, maybe in the future I’ll come back and explain it. Please look at each step and each condition. If you find a mistake, let me know and I’ll fix and upload an updated one.
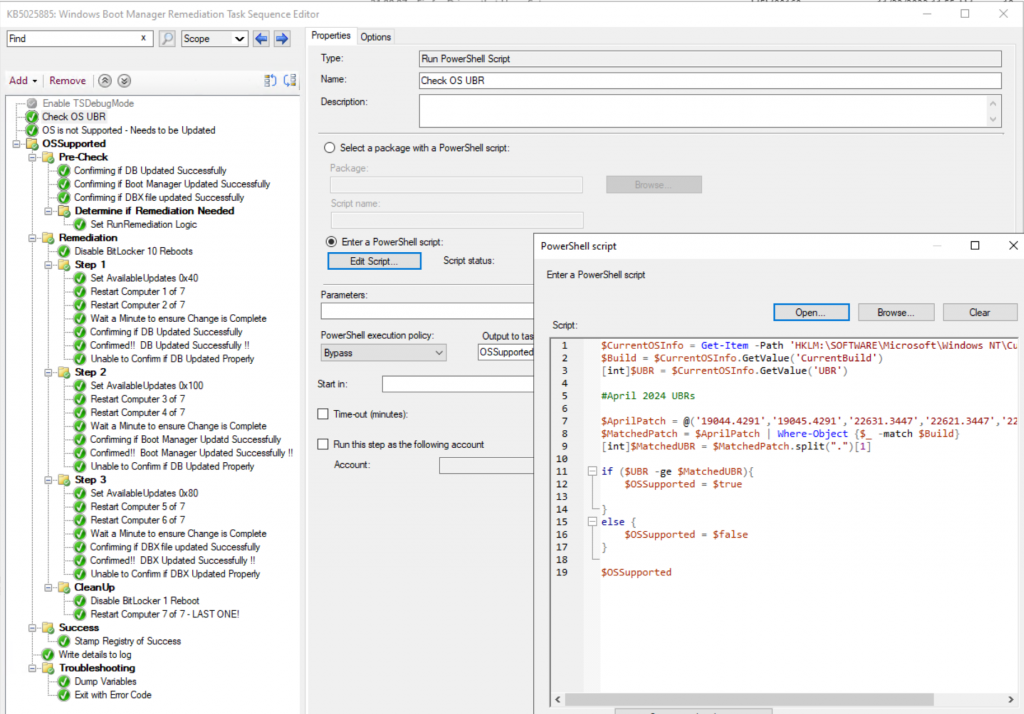
Few notes, this is broken into a few sections,
- OS UBR Check, to ensure the device has the April patch first
- Pre-Check, which will determine if remediations have been completed in the past. Sometimes they could report false when true if the event logs have rolled over, so that’s why there is a Registry Value that we’re tagging at the end of the successful remediation to know the device did in fact get remediated.
- Remediation
- Step 1 – DB Update
- Step 2 – Boot Manager Update
- Step 3 – DBX Update
- Success – Stamps registry that remediation was successful.
- Complete – write info to smsts.log
- FAIL – if fails, dumps variables to a log file and exits with error code.
Walkthrough of Demo via Screen Captures
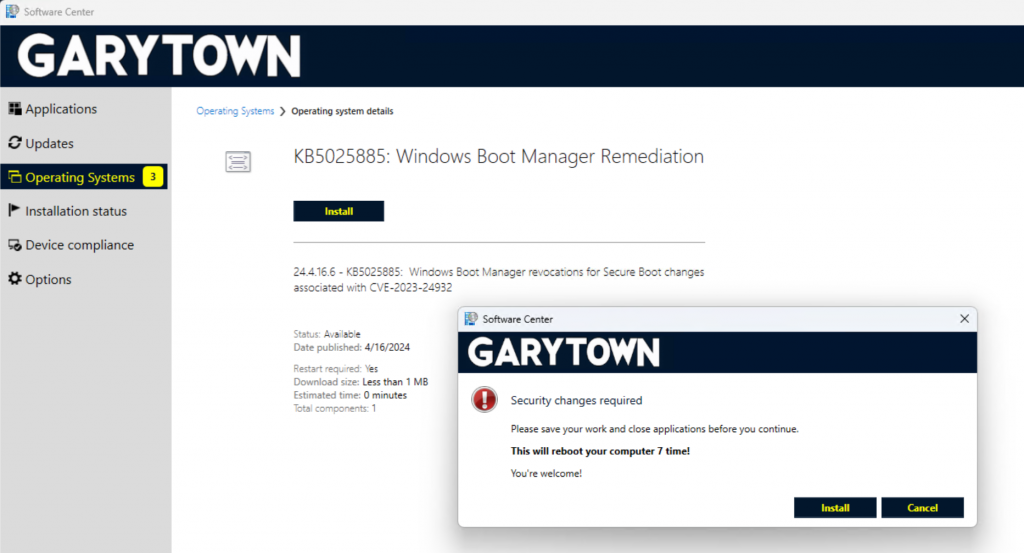
Note, after import, I recommend you go into the properties and update these fields. I’d probably add something like “This will take about 15 minutes, during which time you will not be able to use your computer, please start before heading to lunch or at the end of your work day”
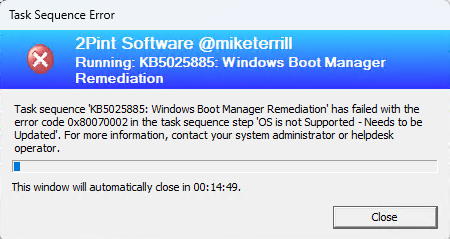
IF the device does NOT have the the April (or better) patch installed, it will fail out:
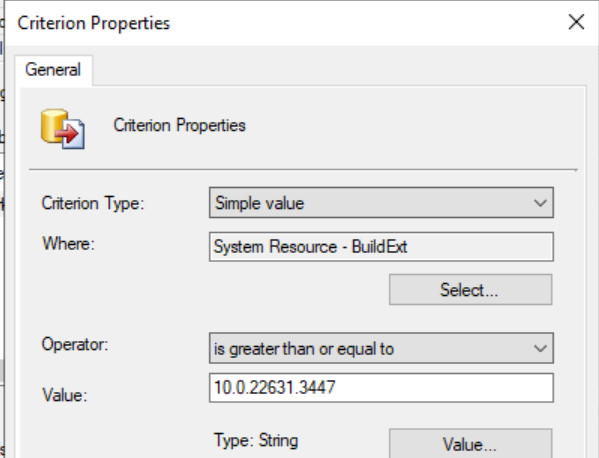
I recommend only deploying to devices that have the April patch. Create a collection query to ensure it only allows devices with the specific builds or higher:
Ok, back to the TS:
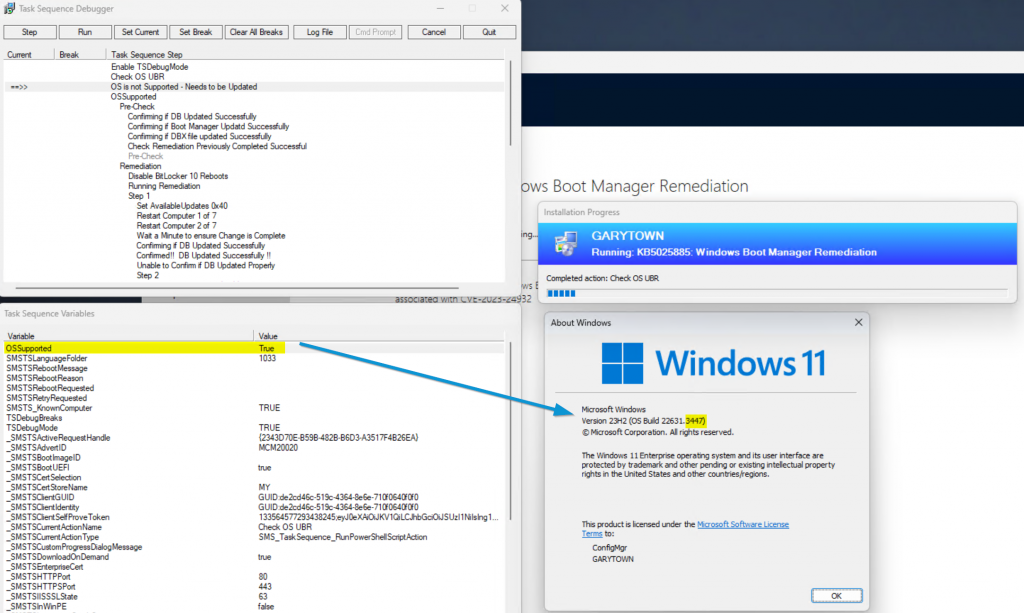
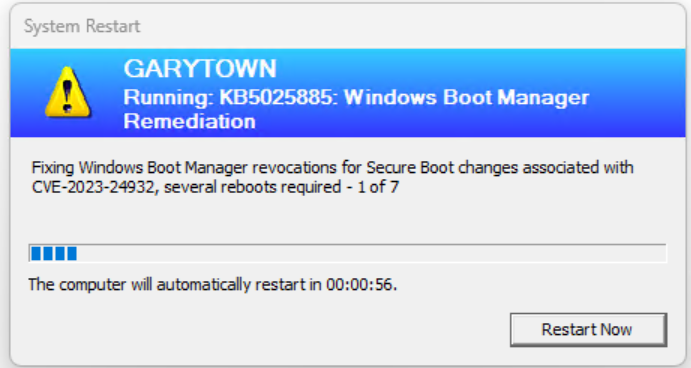
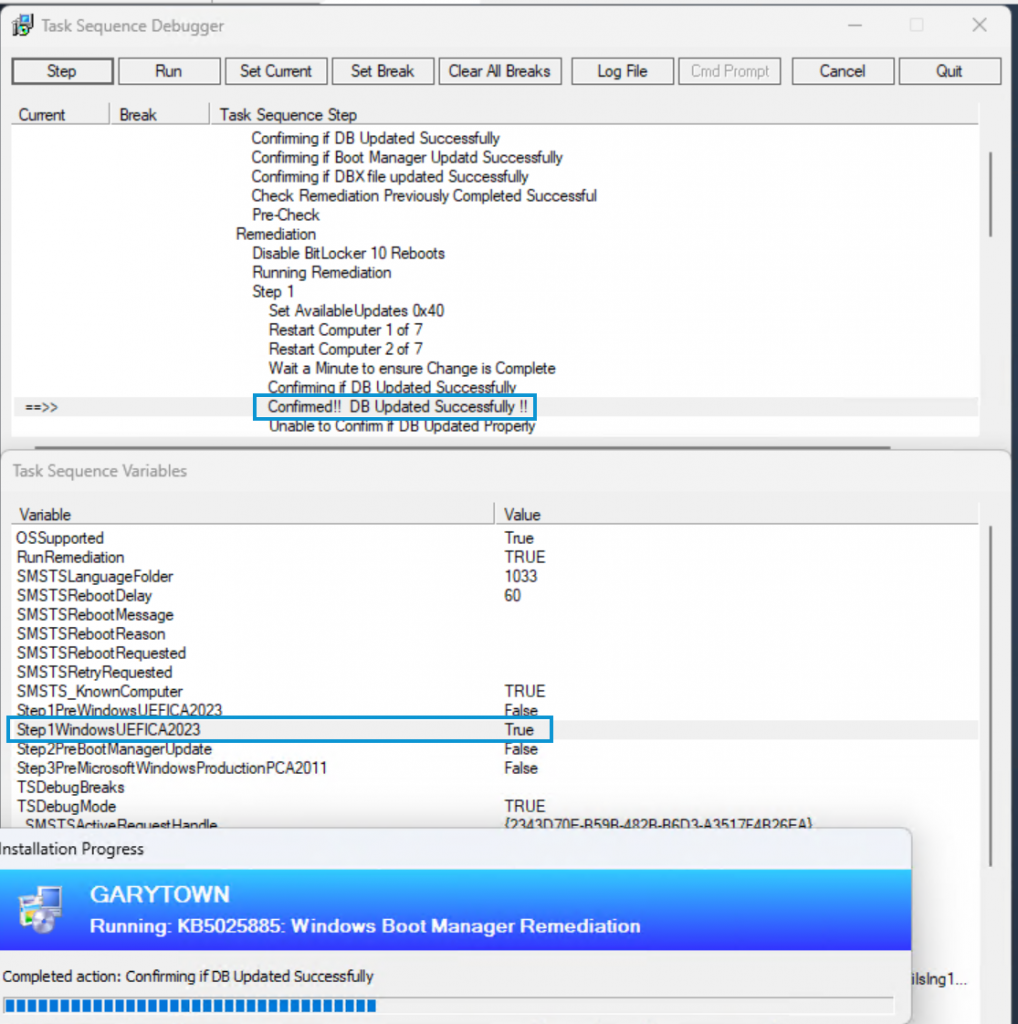
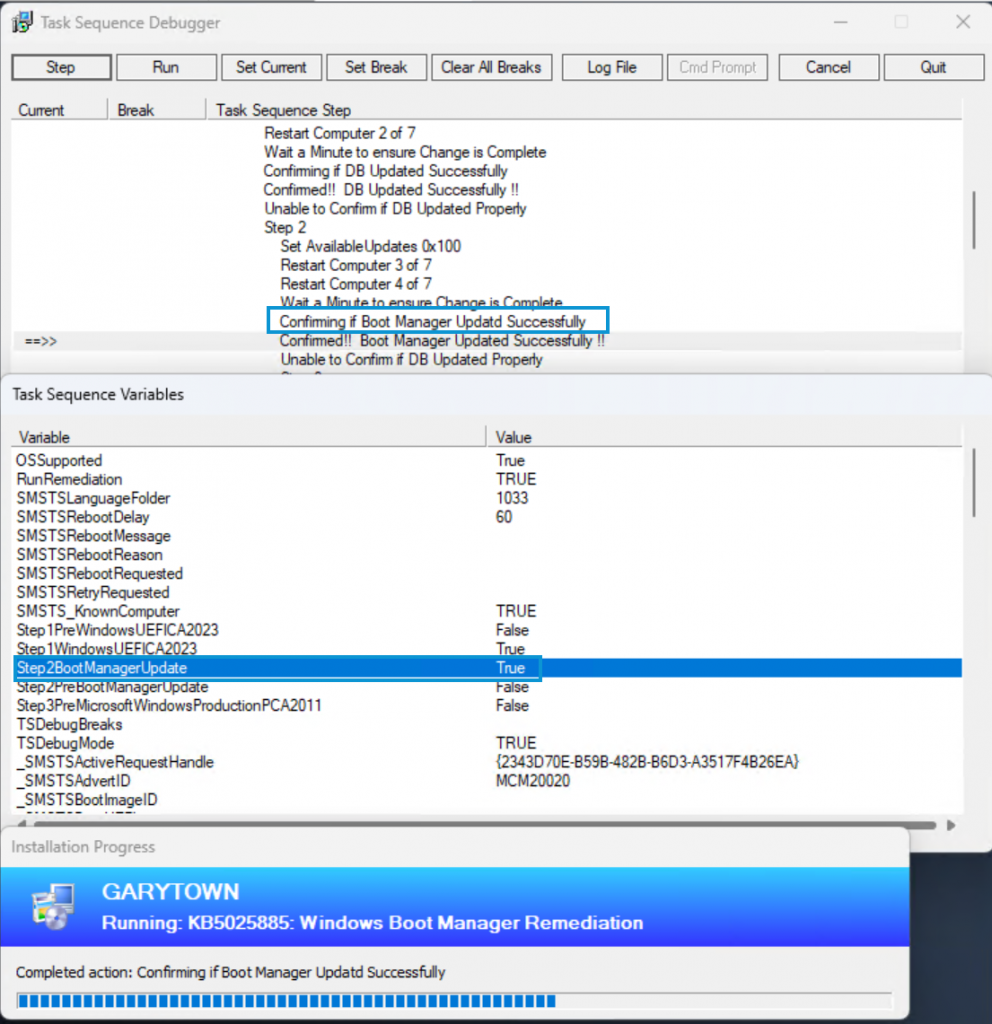
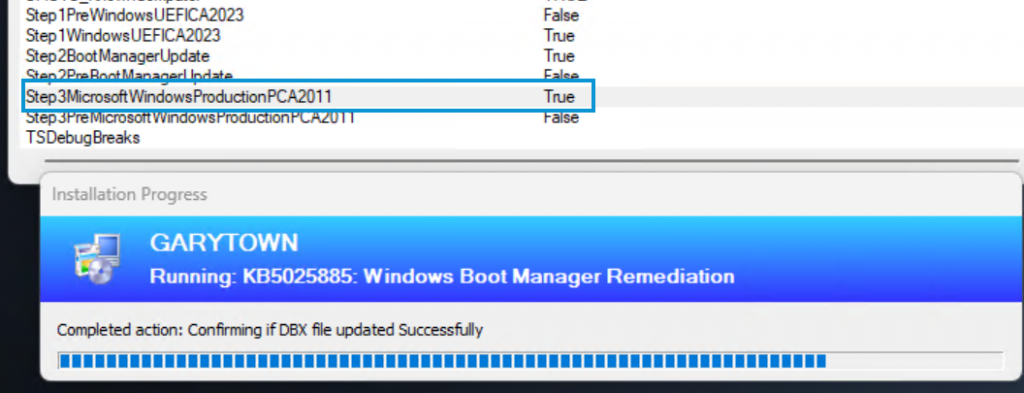
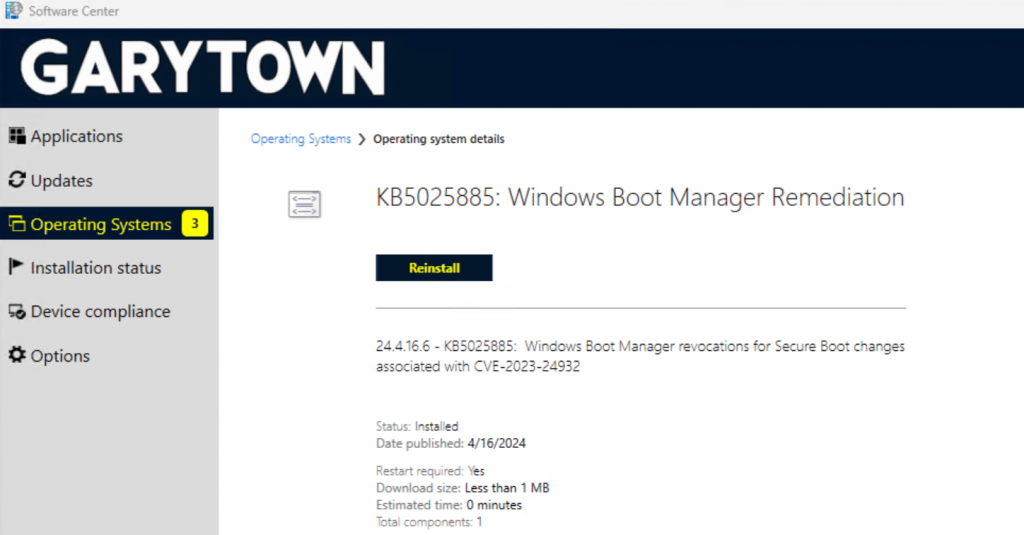
Running again:
Running again on a successful device, will show that the prechecks will let the TS know that it does not need to run the remediation again.
GARYTOWN.COM
Thanks, works a treat. Only issue it doesn’t re-enable Bitlocker from when it suspended.
I think that is just the reboot count, after several reboots I believe Bitlocker is supposed to re-enable. I will try and test. Thanks Gary for working this out. This is such a massive coming change that will affect so many CM admins, that without people like you — I wonder if Microsoft would have just let 1000s of CM environments start having OSD failures this summer. :\
We have ADK 10 in our environment and boot.wim is of version 21H2 and no patch is available for 21H2. Will it affect our environment if I applied all 3 Steps. What action should we take beforehand.
If you apply all 3 steps, it will break your imaging until you update your ADK to a newer version, then patch it to at least April. I would avoid applying all 3 steps until MS provides a better process.
Have you tried ADK 10.1.26100.1 (May 2024) yet on a device that has been through stage 3? Even though MS say no further steps are needed the WnPE media won’t boot, am I missing something?
I have, and it doesn’t work. PXE will require MS to release some sort of update, and if you build a Flash Drive, you still need to update the EFI files.
Ok thanks, I’m glad i’m not going insane over this. It clearly states that nothing further is needed on the webpage and the correct files seem to be present but in EFI_EX folder.
I did find this link which appears to be for OEMs that talks about how to create a compatible WinPE USB, which does work.
https://learn.microsoft.com/en-us/windows-hardware/manufacture/desktop/winpe-create-usb-bootable-drive?view=windows-11#update-the-windows-pe-add-on-for-the-windows-adk
Hello,
Can you still confirm, that is impossible to update the boot image by the secureboot regkey modifications (described in the technet article) and update files for pxe on the configuration manager, and get PXE working on clients which have been upated with the secureboot task sequence above?
Because i do not want to waste time in experimentals for my pxe environment.
I still behold the whole topic and his slowly growing information about it.
To the MSDN Win 11 23h2 iso subject, ms didn’t update their newest ISO Installation media!
There is still an old bootmgr and certificate on the iso!
Perhaps they will only update the coming win11 24h2 source files and his iso.
regards
What about the private users worldwide?
I cannot imagine that every privat device will be update via script oder task sequence, and no user will be able to do the known described steps from ms.
I think ms will fully automate the update process by windows update packages.
Only the restarts are questionable or could be become a little challenge for the developers.
By the way, the task sequence works very good from the begining of the tests.
Congratulations to this master piece of sequence! Great Job. Thanks
MS will slowly enforce all of these settings for everyone, over time. As people naturally reboot their devices, it will slowly get enabled. Just unsure when MS will start enforcement, probably mid/late 2025 is my GUESS.
Should we be using Version 24.1.19.1 task sequence or Version 24.8.29.1?
All depends on what you want to do.
This is the latest: 24.8.29.1
If you don’t want to enable revocations, just make sure step 3 is disabled
Awesome, thanks a bunch!
Cool but what do we do about the bootable media corp wide
Once you’re applied the Revocations, you will need to build new USB Boot media, as PXE will no longer work.
However, you can use 2Pint’s iPXE solution, which works in both scenarios.
Very nice Gary
I’m finding that if you employ the built-in schtask you can get rid of one of the reboots on each pass
Set-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Control\SecureBoot” -Name “AvailableUpdates” -Value 0x40
Start-ScheduledTask -TaskName “\Microsoft\Windows\PI\Secure-Boot-Update”
Sleep 60
reboot
Set-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Control\SecureBoot” -Name “AvailableUpdates” -Value 0x100
Start-ScheduledTask -TaskName “\Microsoft\Windows\PI\Secure-Boot-Update”
Sleep 60
reboot
etc
I’m struggling to apply the mitigations to any devices that have had 2025-03 cumulative patches. Anyone else found this or hopefully found a fix?
Any luck fixing this one cve-2024-21302?
Even when applying https://support.microsoft.com/en-us/topic/guidance-for-blocking-rollback-of-virtualization-based-security-vbs-related-security-updates-b2e7ebf4-f64d-4884-a390-38d63171b8d3 and updating the boot image, the device will simply not boot. I’ve done this previously for KB5025885: How to manage the Windows Boot Manager revocations for Secure Boot changes associated with CVE-2023-24932 without any issues.
That looks like a pain…
I have not touched that CVE yet