Update 4/22/24 – Everything Change in April 2024 – Please see my recent posts:
KB5025885 – Updating your USB Boot Media – Leveraging OSD Module
Rest of this page is basically obsolete at this point. Leaving here for link backs.
Update 9/19/23. Updated ADK Released!
I recently wrote a post for how to apply the remediation in Windows after the May updates, this post now goes on to cover how to update your ADK Winpe.wim file then reload your CM Media to allow it to continue to boot. (ADK = Win11 22H2)
References:
- KB5025885: How to manage the Windows Boot Manager revocations for Secure Boot changes associated with CVE-2023-24932 – Microsoft Support
- KB5025885: Dealing with CVE-2023-24932 via Proactive Remediation & Configuration Items
- David Segura | MVP on Twitter: Here’s some of my notes on CVE-2023-24932
- Automatically update your Configuration Manager boot images for CVE-2023-24932 – Jose Espitia
High Level Overview:
- Install Windows 11 22H2 ADK & WinPE Addon on Windows 11 22H2 machine. [LINK]
- Download: 2023-05 CU for Windows 11 Version 22H2 for x64-based Systems (KB5026372)
- [Script] Backup the ADK winpe.wim file
- [Script] Mount the ADK winpe.wim file
- [Script] Apply the Windows 11 22H2 CU to the mounted media
- [Script] DISM Cleanup
- [Script] Dismount Media
- [Script] Export Image to reduce size
- Copy your updated winpe.wim to your CM Servers and overwrite the winpe.wim in your servers’ adk location
- Reload your CM boot media.
NOTE: I tried to do this directly on the CM Server, but continued to get errors applying the LCU
Following the Process
Script on GitHub: garytown/UpdateADK_winpe_wim.ps1
NOTE, I’ve updated the script on GitHub since posting this, so you will get slightly different results. Change Log for the script is in the script.
Default ADK x64 winpe.wim before applying LCU
Get-WindowsImage -ImagePath "C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\en-us\winpe.wim" -Index 1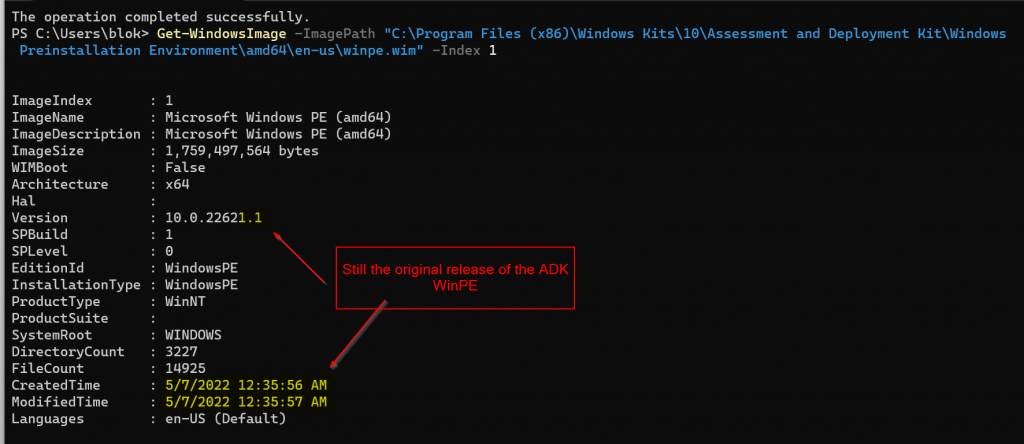
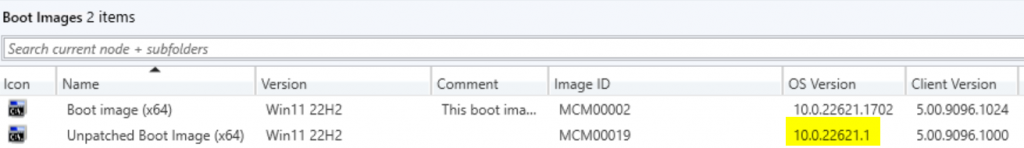
Boot Image in CM will still be 10.0.22621.1
Run the Script
Grab the script on GitHub and update your variables then run.
winpe.wim after:
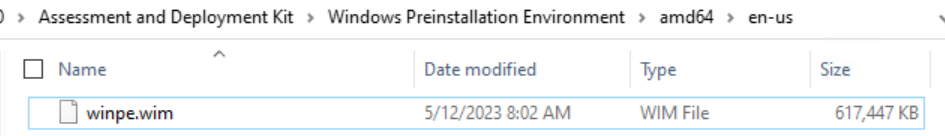
You will see a current date modified and a much larger file.
I then copied that from the Windows 11 device to the CM Server’s ADK install
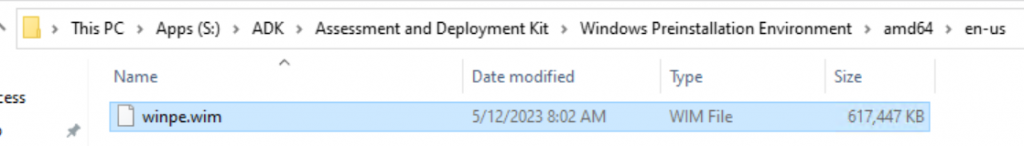
Then in the console, I reload the Media, takes several minutes.
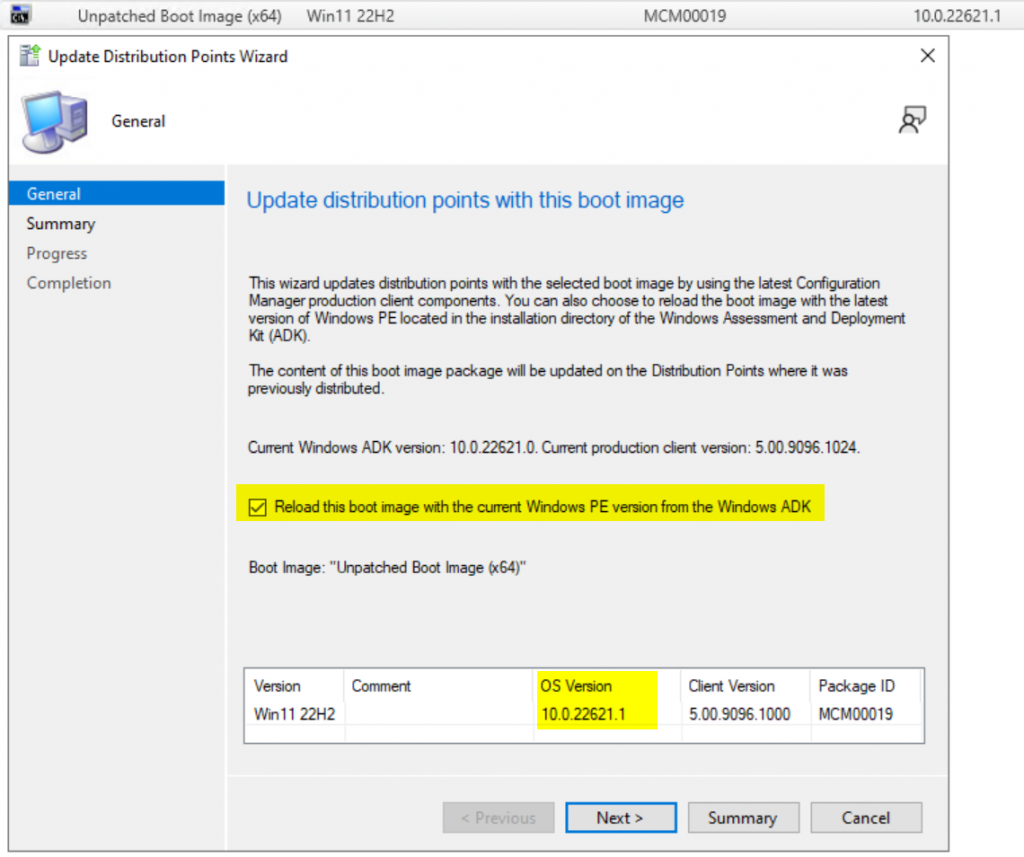
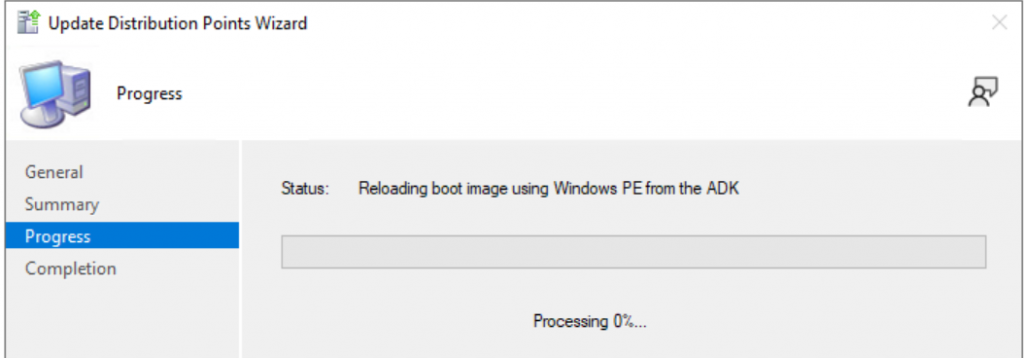
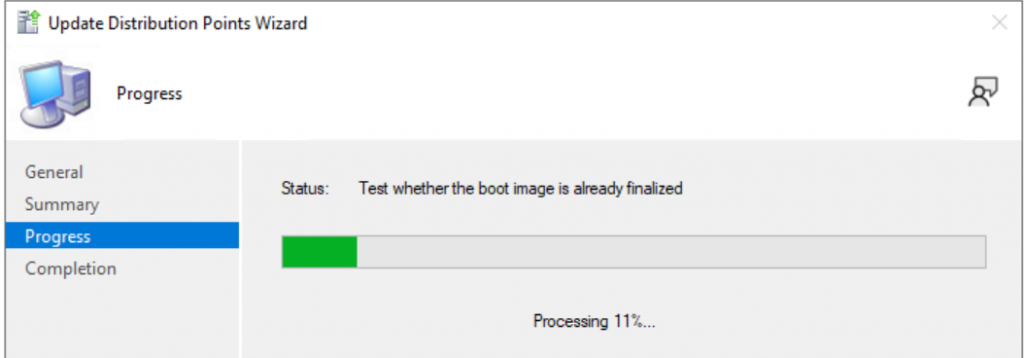
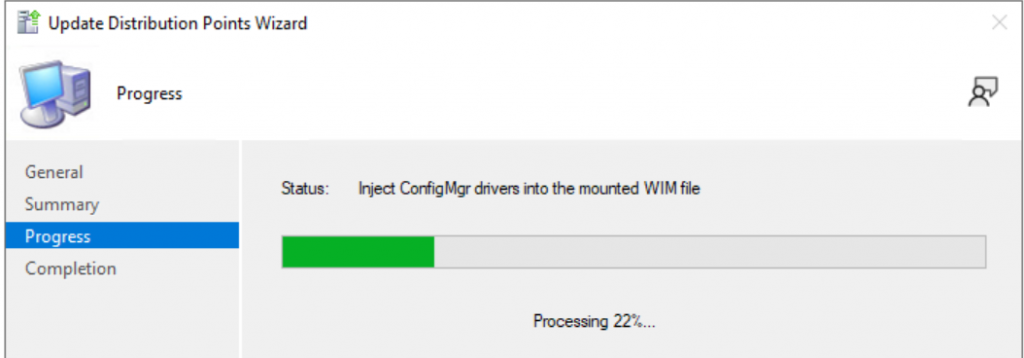
Once completed the boot media will have updated OS Version:
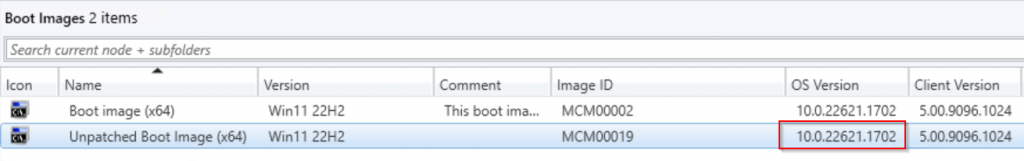
Then I created another Task Sequence Boot Media using the wizard in the console, so now I have my unpatched version and patched version. You can see, the patched version is 150MB larger.
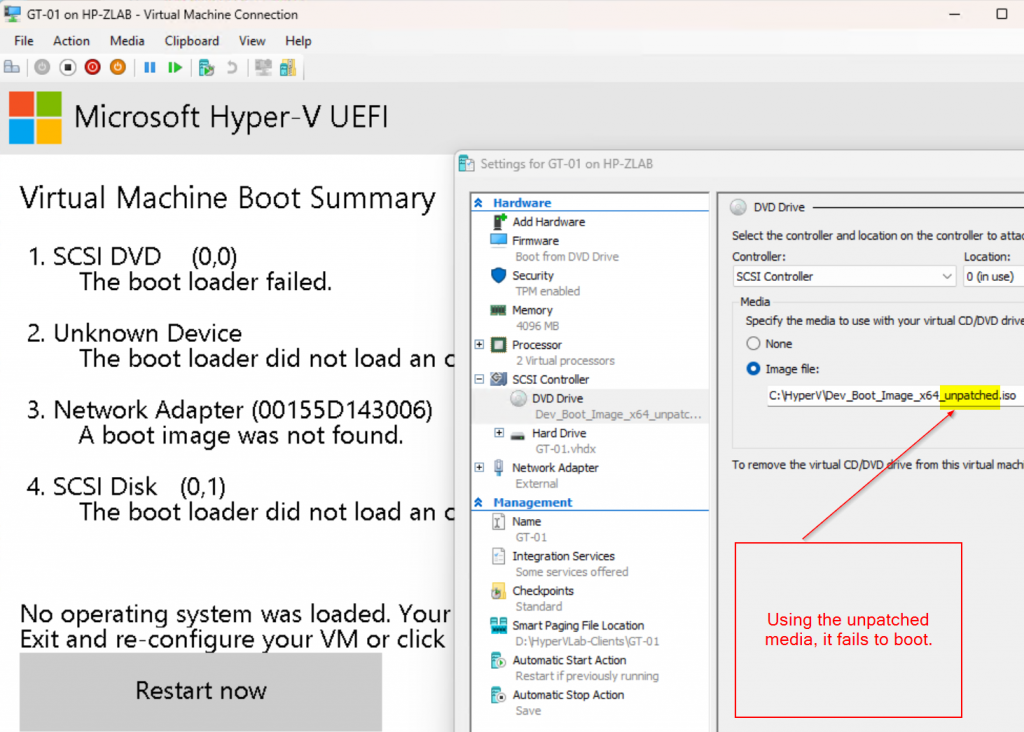
Testing Booting a VM
Test 1: Old Boot Media (unpatched)
Test 2: New Boot Media
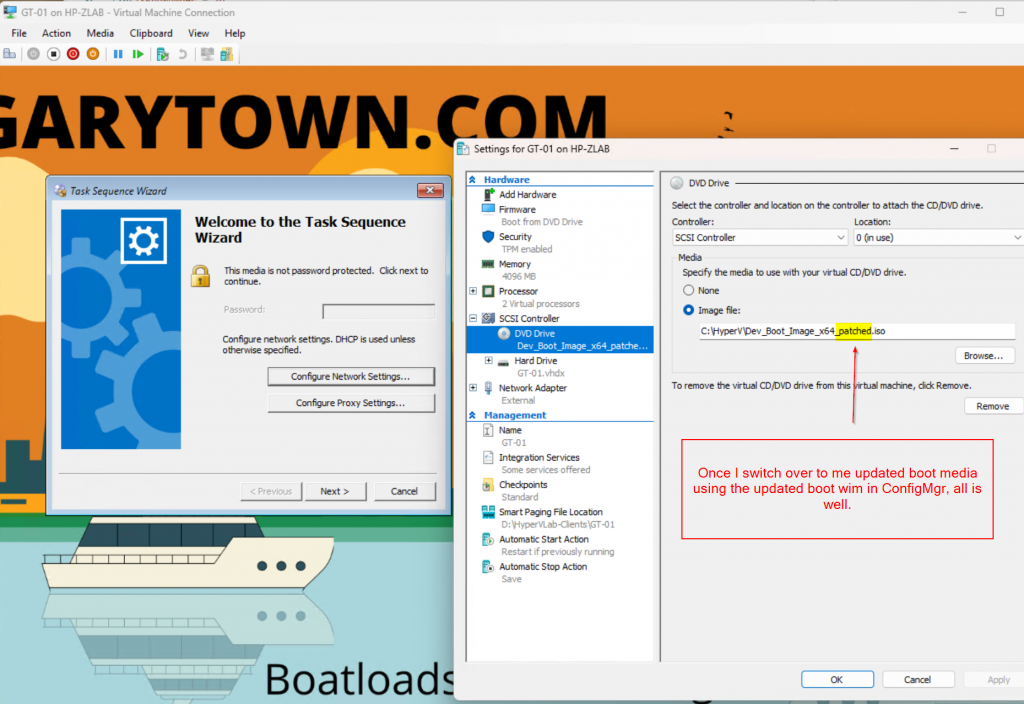
Let me know if you run into any issues, but so far, this has been working for my Boot Media in ConfigMgr.
GARYTOWN.COM
Thanks, we are still running an older ADK version 2004 we are still running W10 only in our environment, shouldn’t be a problem updating the boot image with this version.?
You can deploy Win10 with Win11 ADK
I typically keep my ADK at the latest version ConfigMgr supports. It also makes deploying newer models easier as it has more support built in.
that fine as long as Microsoft support all operating systems they say they do. They don’t and the latest doesn’t work on some server OS’s that still, technically support the site server role.
Hi Gary
During running this section of the script it errors out due to the -DestinationImagePath is empty . Does something need to be there
Export-WindowsImage -SourceImagePath $ADK_WINPE_PATH -SourceIndex $IMAGE.ImageIndex -DestinationImagePath “” -ErrorAction stop | Out-Null
Sorry, I must have missed a control V, it should be set to: “$ExportPath\winpe_export.wim”
I’ve updated the script.
Thank you ,
Microsoft should be releasing an iso with the may update and the Secure Boot bootkit vulnerability fix
Any ideas why I get this:-
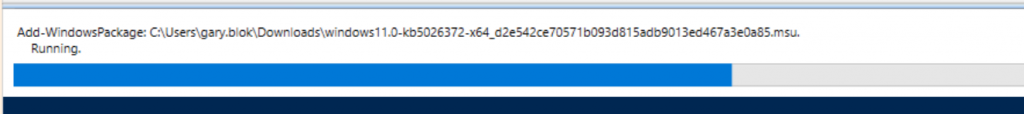
WARNING: Failed to add package C:\temp\windows11.0-kb5026372-x64_d2e542ce70571b093d815adb9013ed467a3e0a85.msu
WARNING: Add-WindowsPackage failed. Error code = 0x80070032
08:06:45: Unable to find the Unattend.xml file in the expanded .msu package.
Add-WindowsPackage : Unable to find the Unattend.xml file in the expanded .msu package.
At C:\Temp\UpdateADK_winpe_wim.ps1:40 char:11
+ try { Add-WindowsPackage -Path $WINPE_MOUNT -PackagePath $LCU_PAT …
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [Add-WindowsPackage], COMException
+ FullyQualifiedErrorId : Microsoft.Dism.Commands.AddWindowsPackageCommand
Are you doing this on a Windows 11 22H2 device? I had similar issues trying to run it on Server OS.
We are still on the last ADK for windows 10 as we had some issues when trying to upgrade to the Windows 11 ADK. I downloaded the appropriate May 2023 KB for windows 10 and patched our boot image using this script. All seemed to be working fine, but builds now fail at the “Setup Windows and ConfigMgr” step. I’m not getting any errors in our OSD task sequence logs, the device just completely fails to reboot. I am using a Windows 10 21H2 image created from the may 2023 Windows 10 ISO, which I assumed would be compatible with the patched Winpe Boot image.
Did you apply the May CU to your Windows 21H2 image?
You’ll need to make sure the build of Win10 is at least 1904X.2965 (MAY) or higher
We created a new Image using the Windows 10 ISO Microsoft released a couple days ago, So I assumed that it already has the May CU applied, and if not, our automated Image creation process would have installed the update. I did roll back to our April 2023 Windows image and encountered the same issue, so I would also assume that it is an issue with my WinPE image and not the OS image. To be an the safe side, I refreshed the install of the Windows ADK and WinPE addon, repatched the WinPE image and crated new boot images.
@Ray.melvin, did you ever get this figured out? I’m in the same boat of trying to get our Windows 10 ADK (10.0.19041.1) up to date, since I’ve seen numerous issues with the Windows 11 ADK. Could you please provide a link to the exact Microsoft Update LCU you were able to install? I’m not having any luck updating mine.
Hi Gary, thank you for this effort. How can I actually see that this .mcu is applied? I can see the modifed date in the .wim file, is there any other options? EFI boot works now, I guess that is the best confirmation?
Once it’s applied to the WIM, you can run the command to get the build number (as shown earlier in this blog), and you’ll see the build number will have been updated.
When I reload will this wipe out my drivers and customization?
No, it will rebuild your Boot Images using the patched media, and re-apply any customizations / drivers you have associated with the boot image in ConfigMgr
I am getting at 0XC0e90002 error it gets past the wds part now but dies on this error this pc has the revocations applied. any Ideas your a life saver thanks
I would make a bootable flash drive based on your boot image as a test to make sure your boot image is working properly. If your current boot image works via USB or ISO on an updated VM with the revocations applied, then I’d suggest redistributing, or perhaps uncheck the box that makes your boot image available via PXE, wait a bit, and check the box again.
I am using a custom image with winpe. If I hit update distro points this will update my image with the new boot changes but not affect my customizations?
When you reload a Boot Image in CM, any customizations that are done via the CM Console are re-applied to the new boot image.
these were done using mdt with winpe addon. Again thanks for the help my pc gets past wds and starts loading my custom wim file then at the end I get the error code above.
Is there a method to make this work with the x86 winpe media?
It should basically be the same, you’d need to download the corresponding CU for your ADK’s WinPE, and DISM it in.
I’ve gone through the whole process,
but when booting from PXE, just before you’d reach the task sequencer page, it reaches windows is starting,
the machine then reboots and tries to boot from PXE source again, ending in a boot loop.
Any suggestions?
Running Configuration Manager 2207
Sounds like a driver issue.
You get the same issue on Hyper-V Virtual Machines and all Models?
I suggest starting with a clean Boot Image (Import a new one and make no modifications), then deploy that as your PXE boot image and see if it work on a VM.
After the update. Did you copy the updated wim to “C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\en-us” on the server? Overwriting the original? Or did you copy to a folder on the server and add the updated wim as a new boot image? Thanks!
Thanks Gary,
Quick question with the CU should we be using this months or still May’s CU, thought they might of updated some components with the latest.
Also just with copying the winpe.wim to CM do you back up the original first just in case you have to rollback?
Cheers for your work
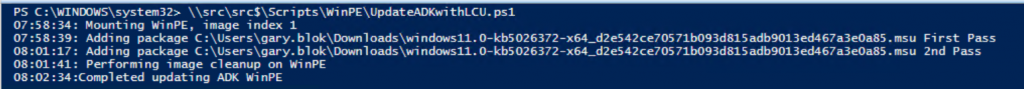
Thanks Gary! I will add a comment here to anyone still using Windows 10 ADK. You need to install the SSU first and then CU. Otherwise it will probably fail. The messages i got initially
WARNING: Failed to add package C:\temp\windows10.0-kb5026361-x64_961f439d6b20735f067af766e1813936bf76cb94.msu
WARNING: Add-WindowsPackage failed. Error code = 0x800f0823
Then i used the same script to add SSU
15:44:11: Adding package C:\temp\ssu-19041.1704-x64_70e350118b85fdae082ab7fde8165a947341ba1a.msu First Pass
15:44:25: Adding package C:\temp\ssu-19041.1704-x64_70e350118b85fdae082ab7fde8165a947341ba1a.msu 2nd Pass
15:44:32: Performing image cleanup on WinPE
15:46:00:Completed updating ADK WinPE
15:46:00: Exporting image to C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\en-us\winpe_export.wim
After success i managed to patch it with CU
15:46:32: Mounting WinPE, image index 1
15:46:45: Adding package C:\temp\windows10.0-kb5026361-x64_961f439d6b20735f067af766e1813936bf76cb94.msu First Pass
15:59:15: Adding package C:\temp\windows10.0-kb5026361-x64_961f439d6b20735f067af766e1813936bf76cb94.msu 2nd Pass
16:07:23: Performing image cleanup on WinPE
16:08:52:Completed updating ADK WinPE
16:08:52: Exporting image to C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\en-us\winpe_export.wim
Hi Gary,
We have updated everything properly WinPE for reference image with MDT and boot images. In a patched computer with the right event viewer code 276 Windows boot manager revocation policy version 0x2000000000002 is applied., we did a reimage with our task sequence. Ended up ok, however event viewe is showing code 277 Windows boot manager revocation policy version 0x2000000002 was not found. It is recommended that it be redeployed. Any advice?
I get past the WDS error and after it loads my wim file it errors out at the end with 0xc0e90002 I have tried everything to fix this this is on a pc that has the revocations applied.
Hi
Microsoft changed the procedure to revoking the current certificate used to sign the bootmanagers and replacing this certificate with a new one. The changes are described under timing of updates in their kb unter 9th April 2024.
So all previous changes of the boot images are obsolete now and the boot images have to be patched with a different procedure again.
Please see my recent posts on the subject.
My recommendations are to only deploy steps 1 & 2 of the recent updates listed in April, skipping Step 3 until MS releases updated ADK / Windows.
There is this file wdsmgfw.efi that ends up in C:\Remoteinstall\SMSboot\x64 folder on distribution point.
It’s the network boot program that is loading in the beginning in my environment to bootstrap everything,
it’s signed with 2011 certificate and when it’s trying to load it, secure boot is not letting it.
I’ve done all of the steps, downloaded new WinPE addon, updated to latest patches.
(Tried the 23H2 Windows 11 cumulative updates, 22H2 Windows 11 cumulative, from 04, 09 2024 and the new ones from 23rd of April).
When the wim is mounted you inspect it and already see in Windows\boot\PXE that this file is not signed with new certificate.