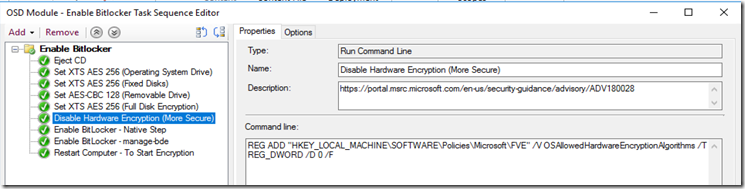
Update 12/20/2018 – Added Step to Disable Hardware Encryption after the vulnerabilities found on several SSD vendors (Screen shot taken from my non-mbam bitlocker sub TS)
Add step “Run Command Line”
REG ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE" /V OSAllowedHardwareEncryptionAlgorithms /T REG_DWORD /D 0 /F
All Steps:
Eject CD
powershell.exe -NoProfile -Command "(New-Object -ComObject 'Shell.Application').Namespace(17).Items() | Where-Object { $_.Type -eq 'CD Drive' } | foreach { $_.InvokeVerb('Eject') }"
Set XTS AES 256 (Operating System Drive)
REG ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE" /V EncryptionMethodWithXtsOs /T REG_DWORD /D 7 /F
Set XTS AES 256 (Fixed Disks)
REG ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE" /V EncryptionMethodWithXtsFdv /T REG_DWORD /D 7 /F
Set AES-CBC 128 (Removable Drive)
REG ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE" /V EncryptionMethodWithXtsRdv /T REG_DWORD /D 3 /F
Set XTS AES 256 (Full Disk Encryption)
REG ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE" /V OSEncryptionType /T REG_DWORD /D 1 /F
Disable Hardware Encryption (More Secure)
REG ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE" /V OSAllowedHardwareEncryptionAlgorithms /T REG_DWORD /D 0 /F
Enable BitLocker - Native Step
Enable BitLocker - manage-bde
manage-bde -on c: -RecoveryPassword
Restart Computer - To Start Encryption
Side note, if you already encrypted using hardware encryption, you’ll have to decrypt first, then encrypt it again after the policy is set, either via GPO or registry. You should set Bitlocker Encryption to software in Group Policy right now!
Original Post:
I’m updating our TS for Windows 10 (1511) and wanted to take advantage the new encryption.
I had to change a few steps, import some keys, and use good old manage-bde, but it’s working, and at the end of the day, it is populating the keys into both AD & MBAM
Issues I ran into was getting it to use full disk encryption, instead of used space only, and getting it to use XTS-AES 256. Hopefully you’ll find this useful.
We are using MBAM 2.5 SP1, ConfigMgr 2012R2 SP1 w/ MDT 2013 U2 Integrated.
Source information I used to help get this working: apppackagetips.blogspot.com & and idea about using Manage-Bde
Assumptions, you’ve already setup your partitions to support Bitlocker – More info here, and You’ve setup your TS to turn on and Activate the TPM Chip in the bios and you have NO “Pre-provision BitLocker” Steps enabled. I had to disable both Pre-provision steps to get this to do full disk encryption:
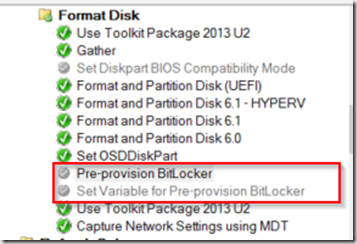
TS Steps for our Enable Bitlocker Steps, this is near the end of the entire TS. (All of the steps I’ve set to continue on Error)
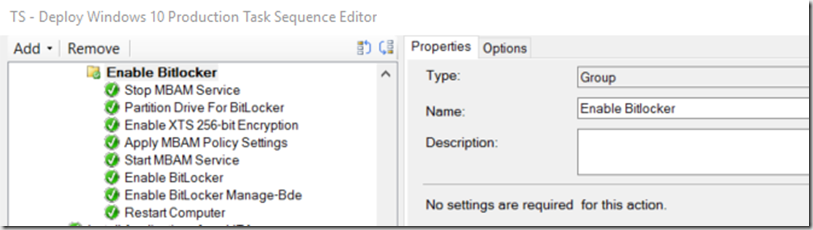
- “Stop MBAM Service” – Since we are using MBAM (which is installed in our actual image), the first step is stopping the MBAM Service (Net stop mbamagent)
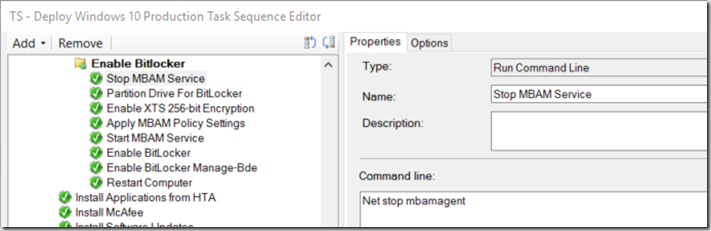
- “Partition Drive for BitLocker” – This is a generic MDT step that I left in. I have not tested to see if I can disable it, but for now, it’s working with it there. – This will cause TS to fail if not set to continue on Error
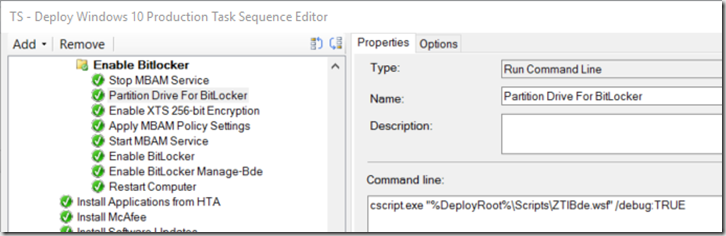
- “Enable XTS 256-bit Encryption” – This imports a registry file with settings needed to use XTS-AES 256 Encryption – Reg File lower in this blog (regedit /s XTS_256-bit.reg)
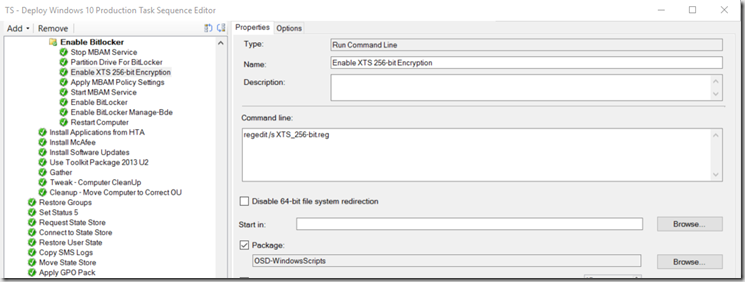
- “Apply MBAM Policy Settings” – This is another registry setting import for MBAM, I could merge the two, but kept them separate for simplicity (regedit /s MBAMSettings.reg)
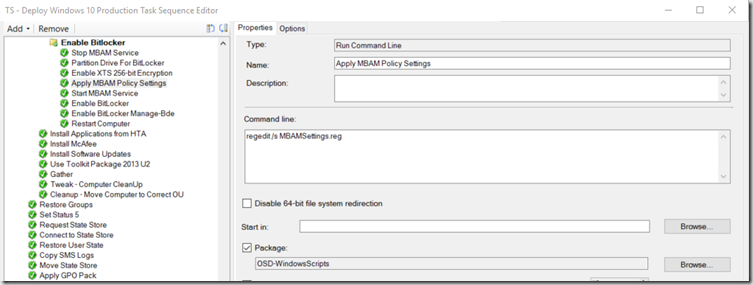
- “Start MBAM Service” (Net start mbamagent)
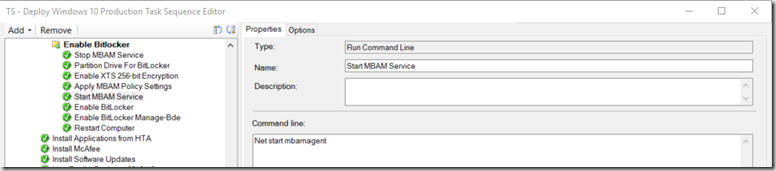
- “Enable Bitlocker” – Generic TS Step – I found that this creates some of the required settings needed, but didn’t actually start the encryption – This will cause TS to fail if not set to continue on Error
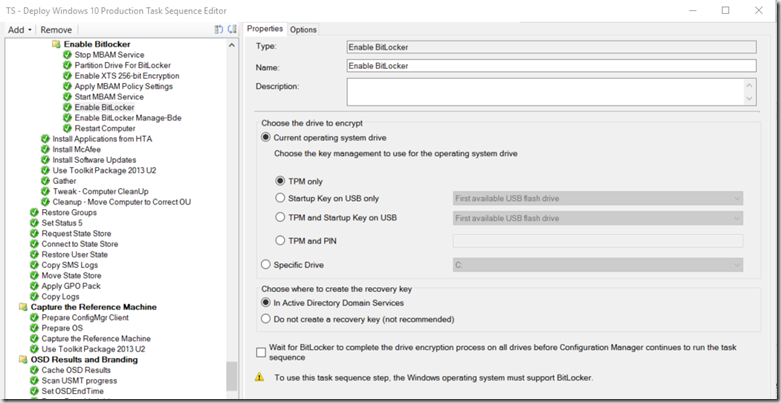
- “Enable Bitlocker Manage-Bde” – This step actually was successful in starting the Encryption Process. Until I added this step, encryption would not start automatically, and I had to manually start it post deployment. (manage-bde -on c: –RecoveryPassword)
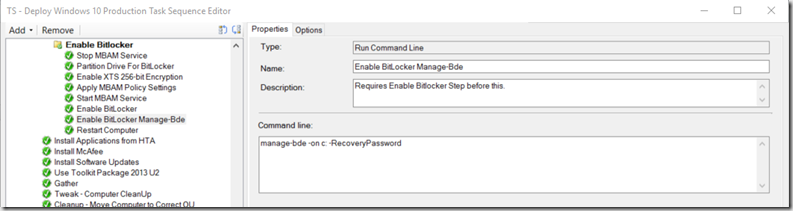
- Restart computer. This kicked in the encryption process.
Registry Files:
XTS_256-bit.reg (I export these settings from a current Windows 10 Client that had bitlocker setup how I wanted via GPO, info found here)
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE]
“EncryptionMethodWithXtsOs”=dword:00000007
“EncryptionMethodWithXtsFdv”=dword:00000007
“EncryptionMethodWithXtsRdv”=dword:00000003
“OSEncryptionType”=dword:00000001
“EncryptionMethod”=dword:00000002
EncryptionMethodwithXts… More info at this TechNet Blog
Registry Key = OSEncryptionType 1 = Full Disk, 2 = Used Space More info HERE
MBAM Settings: (You will need to export this from one of your current MBAM clients, to get the correct Registry data, but here is mine as example – your service endpoint strings will be completely different than the example, as well as other potential differences depending on your Security policy)
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE\MDOPBitLockerManagement]
“UseMBAMServices”=dword:00000001
“UseKeyRecoveryService”=dword:00000001
“KeyRecoveryServiceEndPoint”=hex(2):68,00,74,00,74,00,70,00,73,00,3a,00,2f,00,\
2f,00,6d,00,64,00,68,00,2d,00,6d,00,62,00,61,00,6d,00,32,00,2e,00,6d,00,64,\
00,68,00,2d,00,61,00,64,00,2e,00,68,00,65,00,61,00,6c,00,74,00,68,00,2e,00
“KeyRecoveryOptions”=dword:00000001
“ClientWakeupFrequency”=dword:0000005a
“UseStatusReportingService”=dword:00000001
“StatusReportingServiceEndpoint”=hex(2):68,00,74,00,74,00,70,00,73,00,3a,00,2f,\
00,2f,00,6d,00,64,00,68,00,2d,00,6d,00,62,00,61,00,6d,00,32,00,2e,00,6d,00,\
64,00,68,00,2d,00,61,00,64,00,2e,00,68,00,65,00,61,00,6c,00,74,00,68,00,2e,\
00,73,00,74,00,61,00,74,00,65,00,2e,00,6d,00,6e,00,2e,00,75,00,73,00,2f,00
“StatusReportingFrequency”=dword:0000005a
“ShouldEncryptOSDrive”=dword:00000001
“ShouldEncryptFixedDataDrive”=dword:00000001
“AutoUnlockFixedDataDrive”=dword:00000002
“UseFddEnforcePolicy”=dword:00000001
“FddEnforcePolicyPeriod”=dword:00000000
“UseOsEnforcePolicy”=dword:00000001
“OsEnforcePolicyPeriod”=dword:00000000
“TpmLockoutAutoReset”=dword:00000001
After OSD, and you’ve logged in, you should be able to confirm your settings: manage-bde –status
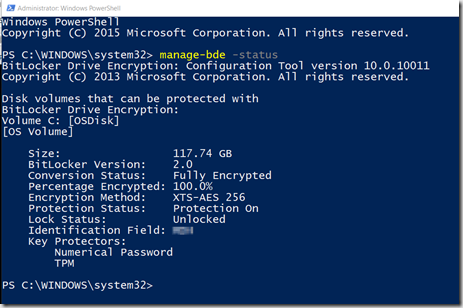
The computer remained on over the weekend, and I then tested recovery from AD & MBAM today… successfully:
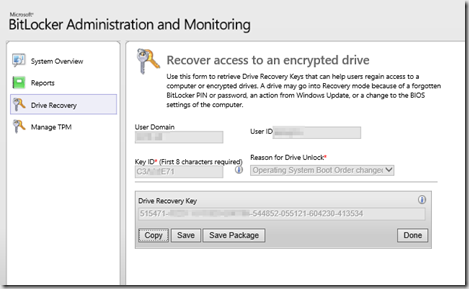
Hope this is useful, I know it’s not really pretty, but it worked for me to get XTS-AES 256 encryption working on Windows 10 (1511), and populating AD & MBAM with the recovery keys.
As always, if you find a way to improve this, or have comments, please post your comments below. I’m pretty good about getting back to you in a timely manner.
Nice post!
You could check out the MBAM Client Scripts which makes it easier to enable bitlocker with a powershell script instead, and it also takes care of the TPM ownership if you are using Pre-Provision bitlocker. It is pretty nice!
https://www.microsoft.com/en-us/download/details.aspx?id=48698
Hey Gary, great article.
Are you using MBAM integration with SCCM? I’ve been noticing a pattern where Windows 10 machines that use XTS-AES 256 are not appearing in the MBAM Supported Computers collection. All my machines that were upgraded from Windows 7 using AES 256 do appear int he collection.
Strange considering the collection query doesn’t look for anything related to encryption ciphers.
Have you run across this as well?
I have not integrated MBAM w/ ConfigMgr. I wasn’t comfortable doing the integration at the time I setup MBAM, and to make life easier replacing my ConfigMgr server in the future, I kept them separated. I currently don’t have any collections for bitlocker. If you figure it out with XTS-AES 256, please reply with your query, I’d like to see that.
Hello Gary, this is realy a very nice article.
How looks the compliance status of your encrypted machines in the MBAM Portal under the subcategory Reports? All my machine which are encrypted with XTS-AES-256 are not compliant with my MBAM-policies. The Portal does not recognize that the policy settings are XTS-AES-256. I’m very confused about that. Do you have an idea or solution about that problem?
Regards Luke
You are correct, MBAM doesn’t support XTS-AES-256 yet, I’m assuming their next update for MBAM will fix this. – https://social.technet.microsoft.com/Forums/Windows/en-US/d343c2bb-864a-4b82-991e-94c3e27e5d16/windows-10-1511-bitlocker-xtsaes-algorithm-and-mbam-25-sp1?forum=mdopmbam
This is a very helpful article. In 1607 Microsoft has made it very hard to capture the TPMOwner password to the MBAM database. Have you successfully done this. Some of my research makes it seem that it is no longer necessary.
We do not capture that. I believe you are correct in that it is no longer needed. We have not needed it in our environment
Hi – Excellent Article. Can we use the same step for the 1703 as well. How about using Invoke MBAM powershell script ? Since I am getting weird results. So we have the following in TS:
1. Convert BIOS to UEFI
2. Set Registry value for XTS_AES256
3. Pre-provision Bitlocker
4. Apply OS
5. Persist TPM Owner with the script SaveWinPETpmOwnerAuth.wsf
6. Apply Drivers/Apps
7. Install MBAM with Dec 2016 Patches
8. Invoke MBAM Script – Invoke-MbamClientDeployment.ps1
After the OS is imaged and when i run the manage-bde -Status C: – I get the following
BitLocker Version : 2.0
Conversion Status: Used Space only Encrypted
Encryption Method: XTS-AES 256
Protection Status: Protection Off
Lock Status: Unlocked
Indentification Field: Unknown
Not sure what is this all about
I see an MBAM error in the event viewer as An error occurred while sending encryption status data – Error Code -2143485933. What could be the possible reason ?
Thanks for a great guide.
The only changes we made was to run the manage-bde step like this:
cmd /c “manage-bde -on c: -RecoveryPassword” >NUL
This will prevent the task sequence from dumping the bitlocker recovery key to the smsts.log in plain text.
We do this so that a user without administrator access can’t boot on usb-media, unlock the hdd and then tweak settings to obtain administrator-rights.
There are probably easier ways of accomplishing this, but it’s better then something.