Ok, so you have HP Devices, and you want to use Sure Recover over WiFi on their newer devices. But it’s a pain to connect to WiFi from the BIOS.
How about, you preconfigure those WiFi SSIDs & Passwords on the devices while they are in the Full OS and working normally, then when you need to use Sure Recover over WiFi, it’s already setup.
Reference Material: c06630499.pdf (hp.com) [Updated 2023.11] – Preboot Wireless Networking on HP Business PCs – Most technical questions can be answered with that document, as well as expanding this to support other Wi-Fi security methods.
Solution Overview
Using ConfigMgr Baselines or Intune Proactive Remediation to regularly check the device, if on WiFi, grab the WiFi profile information and add it to BIOS to be available when needed.
Solution Contents
Process that will set several BIOS Settings:
- Preboot Wi-Fi Master Auto Connect | Enable
- Fast Boot | Disable
- Intel Active Management Technology (AMT) | Disable
- Preboot Wi-Fi Profile # | WiFi Profile Settings
To be able to set the “Preboot Wi-Fi Profile #” BIOS settings, Intel AMT needs to be disabled. If it is Enabled, you will not see those settings available.
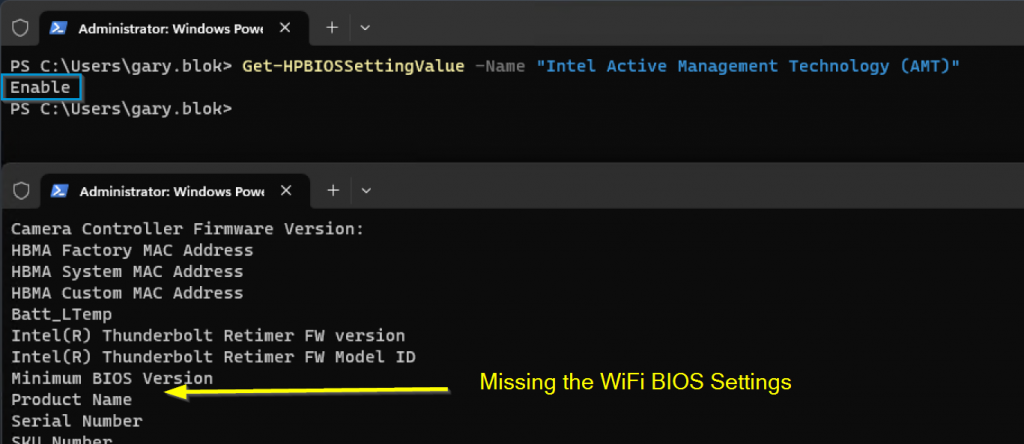
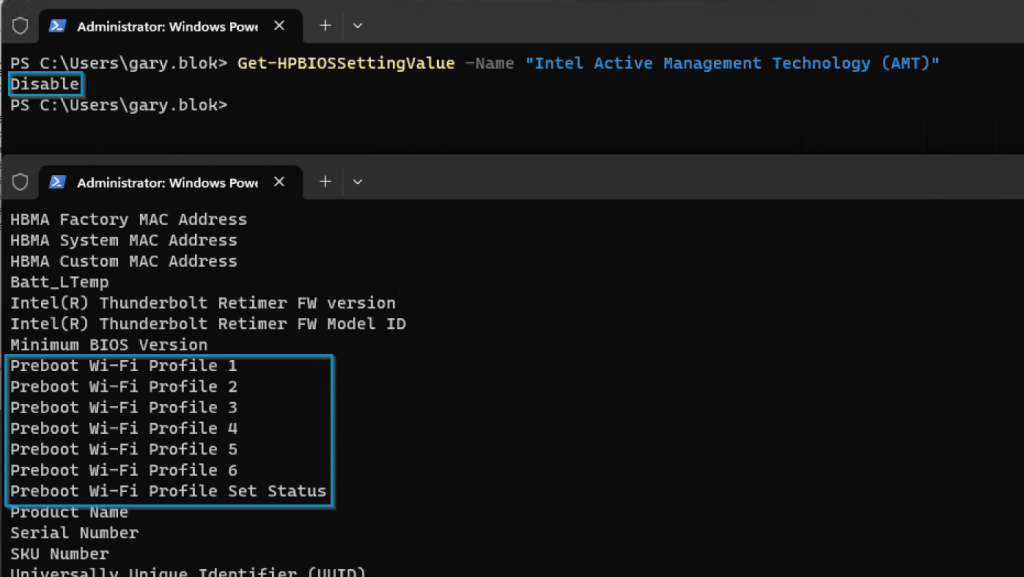
Once disabled, you can then set the Settings with PowerShell as well. I have a custom function that will take the required information, format it how it needs to be formatted, then submit to the BIOS WMI interface.
function Set-WiFiSetPersonalProfile([string]$SSID, [string]$Password,[string]$ProfileNumber,[string]$Type){ #Type is Open or Personal
$bios = Get-WmiObject -Namespace root/HP/InstrumentedBIOS -Class HP_BIOSSettingInterface
$json = '{ "SSID": "' + $SSID + '", "Type": "' + $Type + '", "AutoConnect": "Enable", ' +
'"ScanAnyway": "Enable", "Password": "' + $Password + '" } '
$bios.SetBiosSetting("Preboot Wi-Fi Profile $ProfileNumber", $json, "")
Write-Output "Set Preboot Wi-Fi Profile $ProfileNumber to $json"
}Solution in ConfigMgr
The entire process consists of a few Configuration Items, and one Baseline targeted to HP Devices.
Download the Baseline Export from GitHub: garytown/hardware/HP/SureRecover/CI
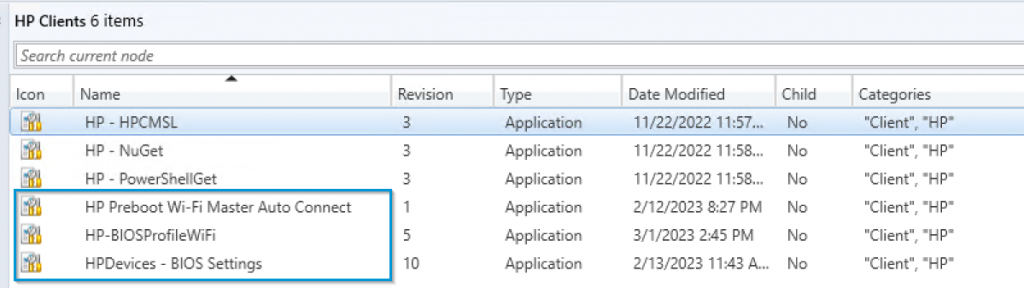
Some of the settings are broken out, so I can control the detection method on each one. I don’t need all of those settings to run on each machine, so I have specific detection method on each Configuration Item to ensure it only runs on machines compatible.
My solution to set HP BIOS Settings is borrowed from Mike Terrill’s Blog, I’d recommend looking over this post to get a deeper understanding of setting BIOS config with PowerShell: Configuring WoL with CM for HP Desktops – Part 2 | Mike’s Tech Blog (miketerrill.net)
I then deploy that Baseline to my HP Devices Collection.
Non-Compatible Endpoint
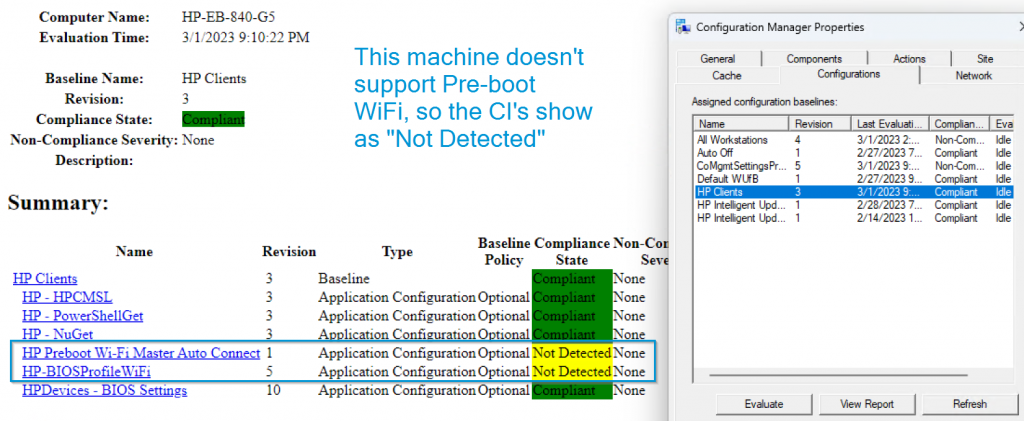
On an HP device that doesn’t meet the requirements to support Preboot WiFi, instead of saying non-compliant or compliant, due to the specific detection methods on the CIs, it will show as “Not Detected”. Example device: HP EliteBook 840 G5
Compatible Endpoint
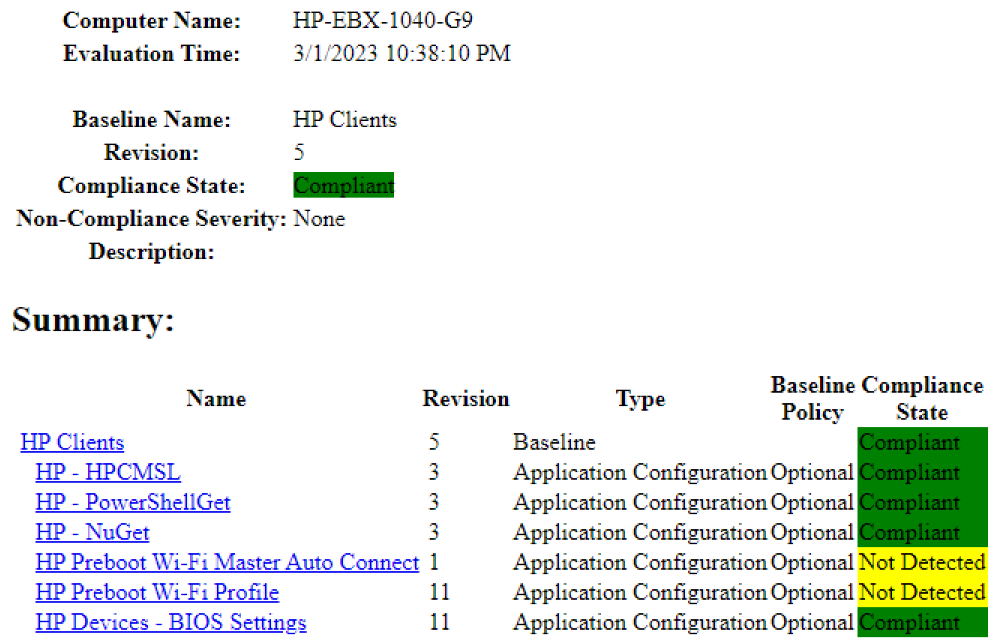
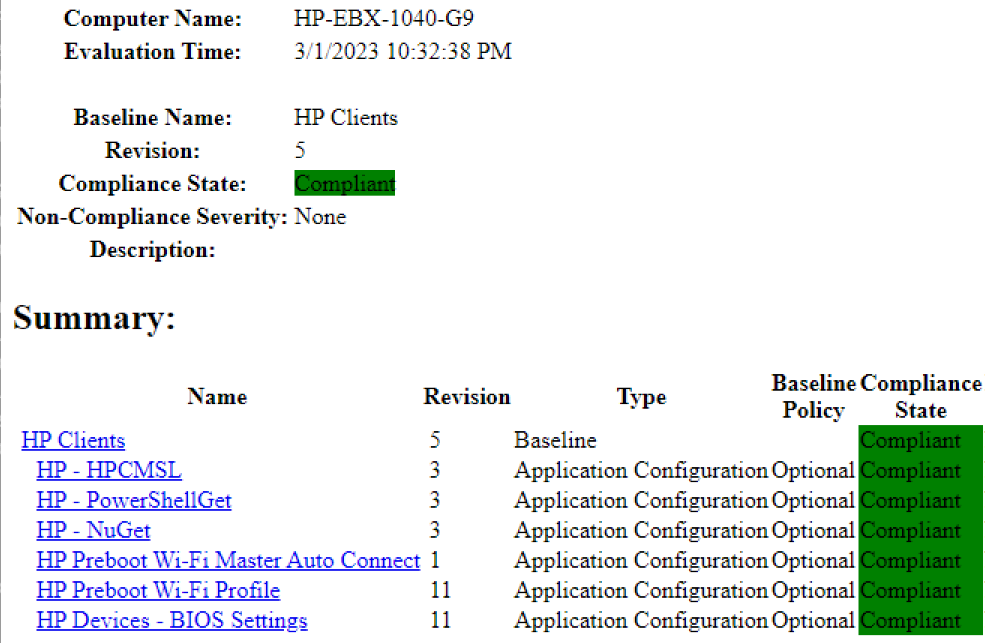
On a device that is compatible, it is possible that the BIOS Profile CI will come back as “Not Detected” if Intel AMT is still Enabled. So after the Baseline runs to disable AMT, and the machine reboots for that to take effect, the CI will go from “Not Detected” to “Compliant”
Reporting in ConfigMgr
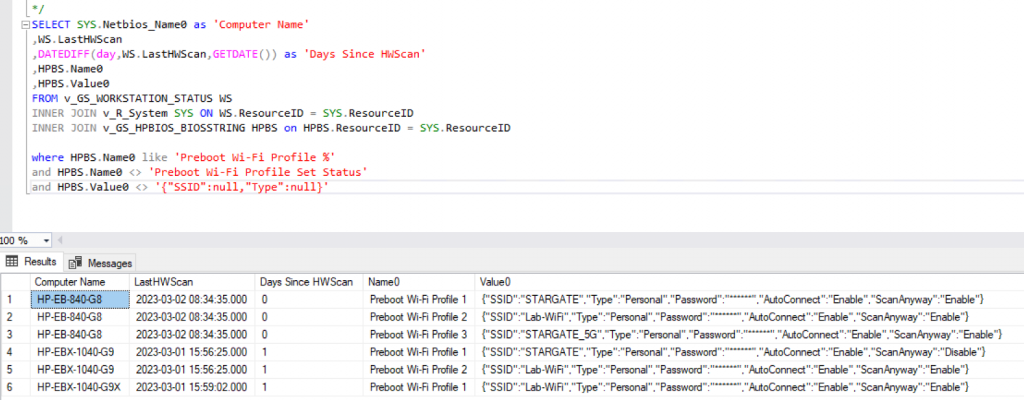
Now that you’ve been running this for awhile, and if you’ve implemented my last blog post about capturing hardware inventory. HP Devices – Inventory BIOS Settings in ConfigMgr – GARYTOWN ConfigMgr Blog. In the image below, you can see my 3 test devices have been a
Solution in Intune
Consists of 2 different proactive remediations. One that sets the BIOS Settings required for enabling the ability for Preboot WiFi, and then another for grabbing and saving the WiFi profiles from the Full OS to the BIOS. Scripts on GitHub: /hardware/HP/SureRecover/PR
Note, script names on GitHub don’t match images below, but it all makes sense when you look at them on GitHub.
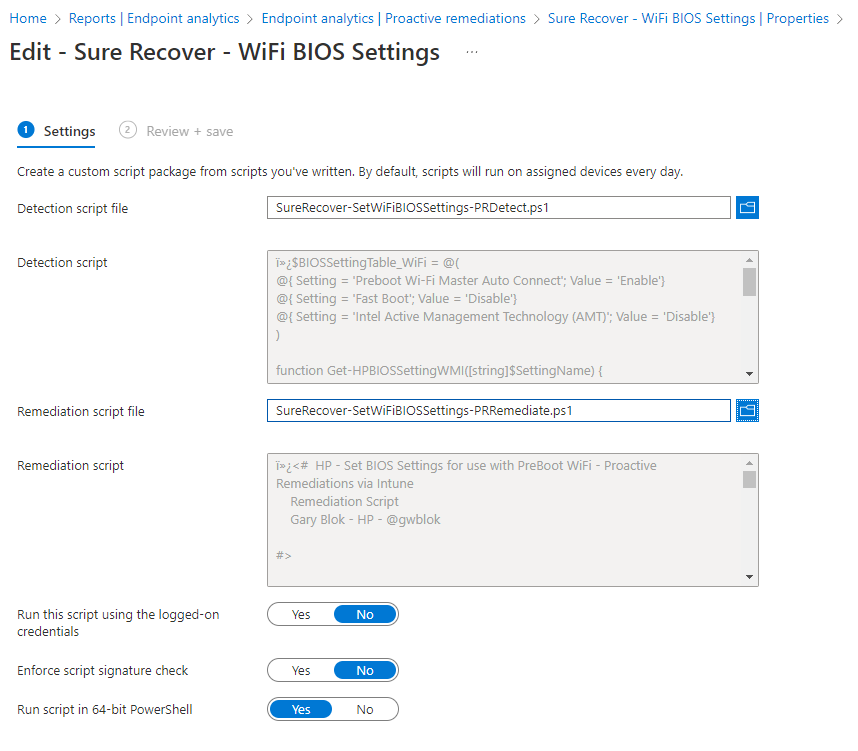
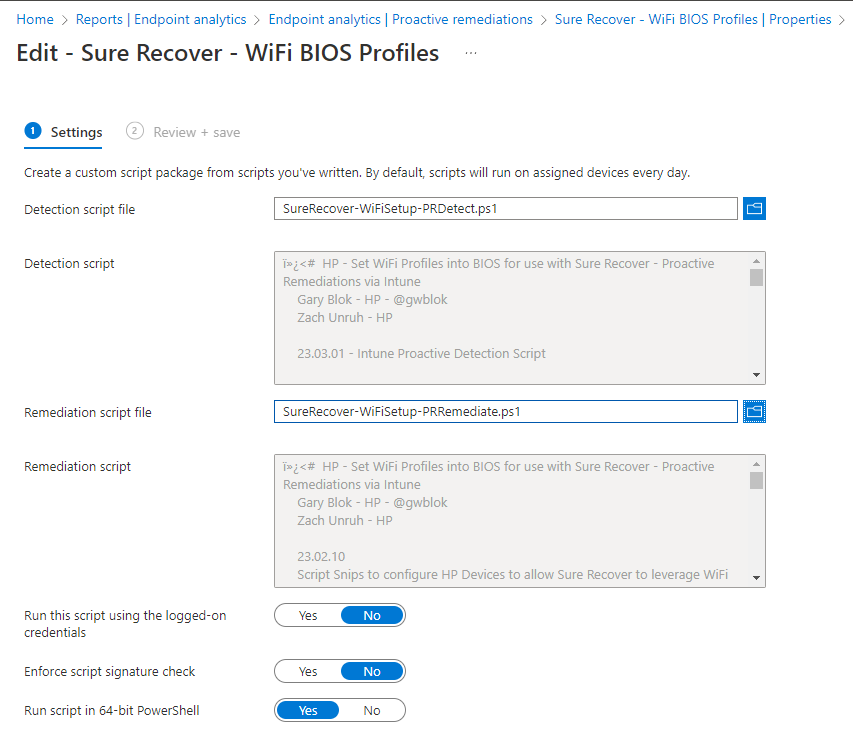
At this point, it’s setup and you just wait and things should start populating. If you want reporting, I’d recommend starting with this: Enhance Intune Inventory data with Proactive Remediations and Log Analytics – MSEndpointMgr, then modify that to grab the HP BIOS Settings you want to inventory.
Checking Settings on Endpoint via PowerShell
From the scripts I’ve posted, you can grab the “Get-WiFiBIOSProfiles” Function, and run it like so:
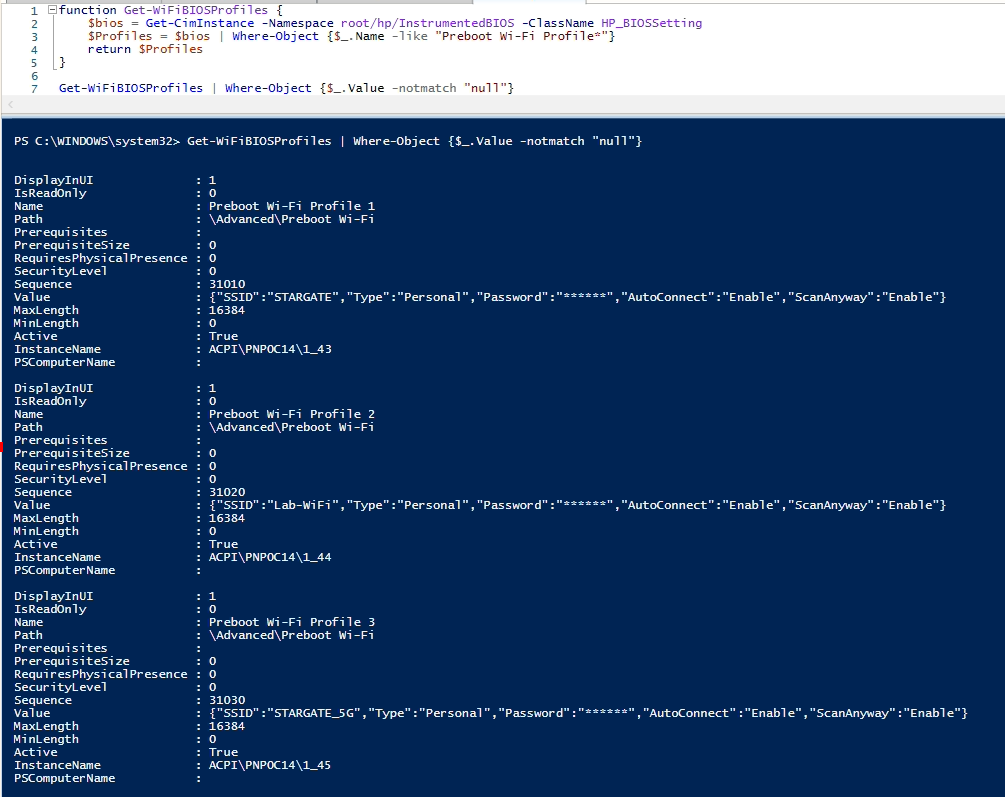
Checking Settings on Endpoint via 3rd Party ROM [F3]
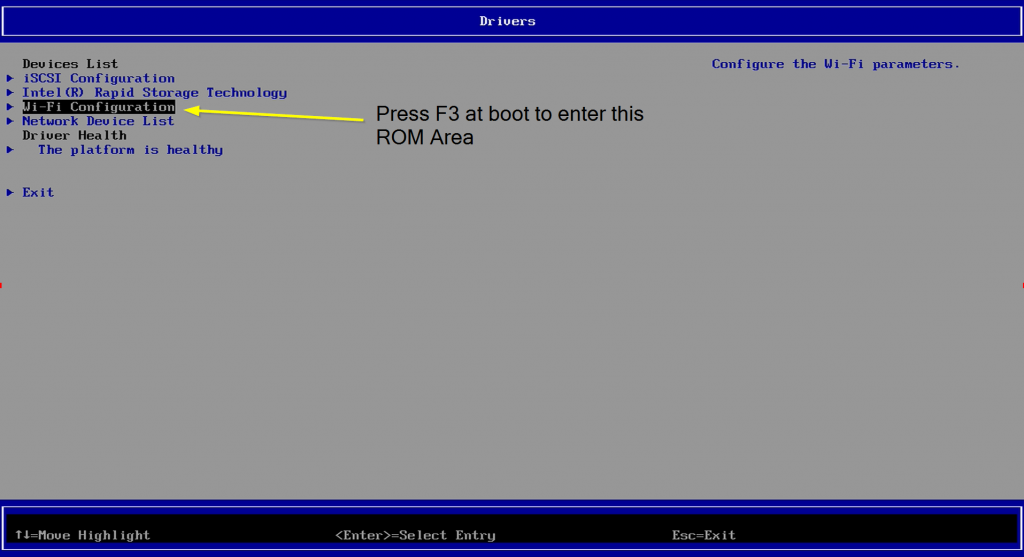
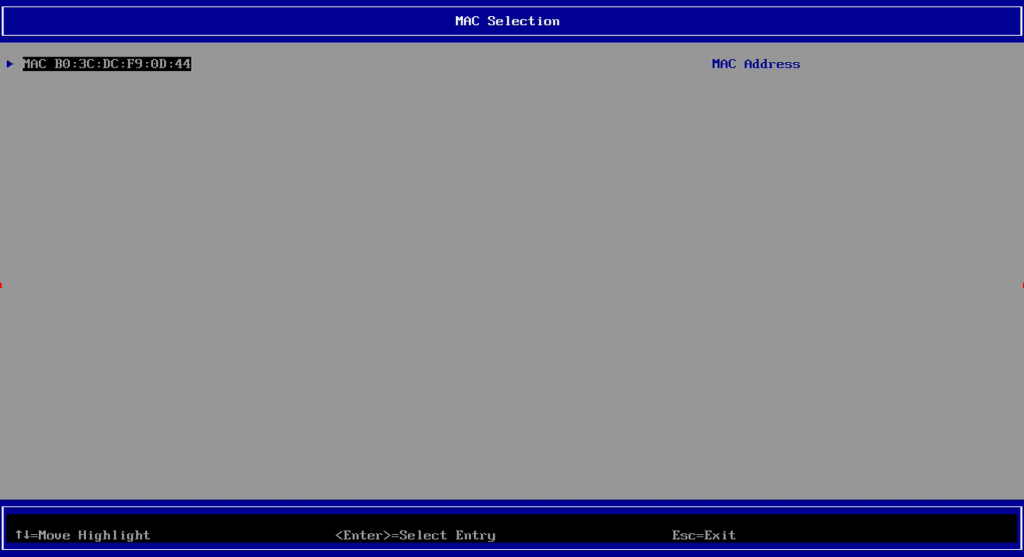
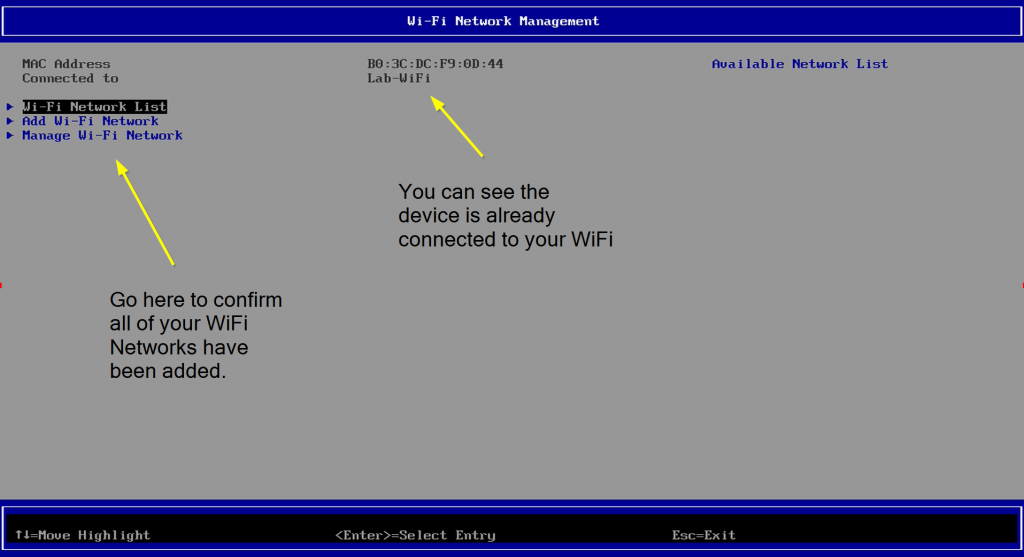
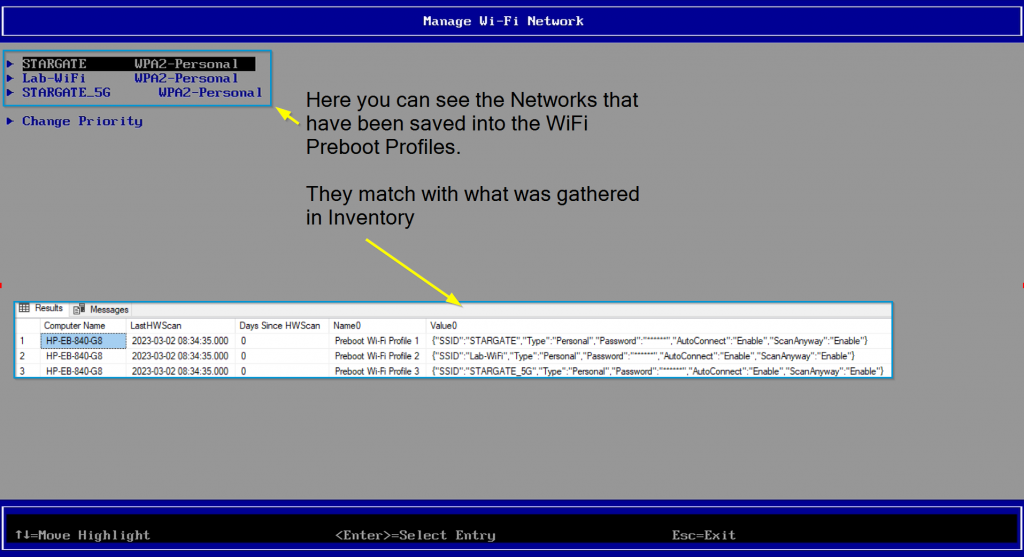
From that 3rd Party ROM area, you can see the WiFi networks, the connection status, and the priority order. You can change the order here, or back in Windows by adding them into the Profiles in the priority you want.
Having done this will enable Sure Recover over WiFi, or PXE over WiFi




Please let me know if you run into any issues.
My Recommendation though.. use Wired Ethernet Connection, if your device didn’t come with one, use a USB -> Ethernet Dongle. While HP will only recommend/support HP Branded, I’ve had good luck with off brand as long as they have Realtek chipset. [Realtek RTL8153 Chipset]
GARYTOWN.COM
very interesting..
can this also be used for OSD and SCCM or does it just work with Sure recover?
You could use it with OSD, you’d just have to add WiFi drivers into your Boot Media and have a way for that to Auto Connect to your WiFi