For those of you who have Active Kill Disk, and want to automate it with ConfigMgr, this is how I’ve done it. This is very similar to the sdelete TS I made, however sdelete was not approved by our security team, so I had to reinvent with Active Kill disk. Active Kill Disk did offer some additional functionality, so I’ve redone this post with Active Kill Disk for those of you who might want to try this.
- First, install Active Kill Disk and Register it on a Test Computer
- On your Source Server, create a Folder where you will keep the Package Contents
- Copy the Files from your test machine to your Package Folder
- C:\Program Files\LSoft Technologies\Active@ KillDisk Suite X.X (Use 9.2 and above to support x64 Boot Media)
- Skip the KillDiskBootDisk.iso file
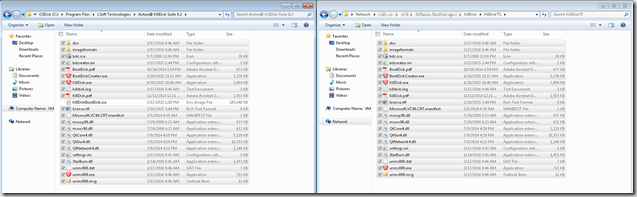
- Next we’ll use a Batch File that will run the process and log the results to the server.
- Download Scripts here (Contents shown below), and add it to your Package Source
- Create a Package in ConfigMgr, (no program), and distribute the contents. You’ll then point your TS at this package to grab the files needed.
Echo off
REM Script to Wipe Computer using Active KillDisk to meet State Requirements
REM Creates Logs on Network Drive (L:) Which you map in a task sequence step before the Script.
REM FingerPrints Computer with Wipe Results.
REM Created 08.01.2014 by Gary Blok
REM Create FlashDrive Removal Warning:
echo Remove Flash Drive From Machine if Present and Close this Box >>X:\Windows\FlashWarning.txt
echo Will Automatically Continue in 30 seconds >>X:\Windows\FlashWarning.txt
echo Flash Drive WILL BE ERASED if NOT Removed >>X:\Windows\FlashWarning.txt
start X:\Windows\FlashWarning.txt
REM Poor Mans way to pause the script for a short period allowing users to remove the flash Drive.
ping 10.1.1.1
REM – MAP NETWORK DRIVE FOR LOGS (Done in TS Step)
REM net use l: \\server.fqdn\DiskWipeResults /user:domain\useraccount PASSWORD REMOVED (in TS NOW)
REM – RUN KILLDISK PROCESS
REM Options = -ea (Erase all Disk)
REM Options = -em=3 (US DoD 5220.22-M ECE (7 passes, verify)
REM Options = -bm (BatchMode = no user interaction)
REM Options = -fp (Finger Print = When computer boots, displays when it was wiped)
REM Options = -logpath & -certpath (Path were it will save the files)
%WinDir%\killdisk.exe -ea -em=3 -bm -fp -logpath=l:\ -certpath=x:\
REM – SET VARIABLE FOR TAG – Rename PDF File and Copy to Folder on Server (L:\Certificates)
REM http://killdisk.com/killdisk-faq.htm#serial
For /f “skip=2 tokens=2 delims=,” %%i in (‘wmic bios get serialnumber /FORMAT:csv’) do (set “servicetag=%%i”)
ren x:\*.pdf ServiceTag-%servicetag%.pdf
copy x:\*.pdf l:\Certificates\ /Y
REM – Append the ServiceTag number to the KILLDISK.LOG file (including date/time stamp) on Server (L:\KILLDISK.log)
echo %date:~4,10% %time:~0,10% ServiceTag#: %servicetag% >> l:\KILLDISK.LOG
echo ———————————–END OF WIPE PROCESS FOR %servicetag%——————————————- >> l:\KILLDISK.LOG
echo .>> l:\KILLDISK.LOG
echo .>> l:\KILLDISK.LOG
echo .>> l:\KILLDISK.LOG
echo ———————————–NEXT WIPE PROCESS STARTS HERE————————————————– >> l:\KILLDISK.LOG
REM – SET VARIABLES FOR REPORTING
for /F “skip=2 tokens=2 delims=,” %%A in (‘wmic systemenclosure get serialnumber /FORMAT:csv’) do (set “serial=%%A”)
set serial=%serial:~-15%
for /F “skip=2 tokens=2 delims=,” %%A in (‘wmic csproduct get vendor /FORMAT:csv’) do (set “compvendor=%%A”)
for /F “skip=2 tokens=2 delims=,” %%A in (‘wmic csproduct get name /FORMAT:csv’) do (set “compname=%%A”)
for /F “skip=2 tokens=2 delims=,” %%A in (‘wmic CPU get name /FORMAT:csv’) do (set “CPUname=%%A”)
for /F “skip=2 tokens=2 delims=,” %%A in (‘wmic computersystem get totalphysicalmemory /FORMAT:csv’) do (set “memory=%%A”)
set /a memory = memory / 1048576
for /F “skip=2 tokens=2 delims=,” %%A in (‘wmic diskdrive get size /FORMAT:csv’) do (set “hddsize=%%A”)
set hdd=%hddsize:~0,-4%
set /a hdd=hdd/1048576
set TimeStamp=%DATE:~10,4%%DATE:~4,2%%DATE:~7,2%
REM Creates Network Log File (L:\DiskWipeResults.log) and appends information
echo. >>l:\DiskWipeResults.log
echo Date: %TimeStamp% >>l:\DiskWipeResults.log
echo Serial: %serial% >>l:\DiskWipeResults.log
echo Vendor: %compvendor% >>l:\DiskWipeResults.log
echo Model: %compname% >>l:\DiskWipeResults.log
echo CPU Type \ Speed: %CPUname% >>l:\DiskWipeResults.log
echo Memory: %Memory%MB >>l:\DiskWipeResults.log
echo HDD Size: %hdd%GB >>l:\DiskWipeResults.log
echo ____________________________________________________________ >>l:\DiskWipeResults.log
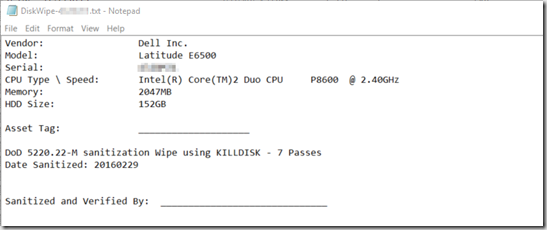
REM Creates Network Label for Machine – (L:\DiskWipe-SerialTag.txt) – Print & Fillout and Tape to Physical Machine
echo Vendor: %compvendor% >>l:\DiskWipe-%serial%.txt
echo Model: %compname% >>l:\DiskWipe-%serial%.txt
echo Serial: %serial% >>l:\DiskWipe-%serial%.txt
echo CPU Type \ Speed: %CPUname% >>l:\DiskWipe-%serial%.txt
echo Memory: %Memory%MB >>l:\DiskWipe-%serial%.txt
echo HDD Size: %hdd%GB >>l:\DiskWipe-%serial%.txt
echo. >>l:\DiskWipe-%serial%.txt
echo Asset Tag: ____________________ >>l:\DiskWipe-%serial%.txt
echo. >>l:\DiskWipe-%serial%.txt
echo DoD 5220.22-M sanitization Wipe using KILLDISK – 7 Passes >>l:\DiskWipe-%serial%.txt
echo Date Sanitized: %TimeStamp% >>l:\DiskWipe-%serial%.txt
echo. >>l:\DiskWipe-%serial%.txt
echo. >>l:\DiskWipe-%serial%.txt
echo Sanitized and Verified By: ______________________________ >>l:\DiskWipe-%serial%.txt
REM Creates Local Log file that displays at end of Process on the Screen.
echo Disk Wipe Complete, Please Record Data for Records >>X:\Windows\JobComplete.txt
echo This computer has finished with a DoD 5220.22-M sanitization of the local hard drive. >>X:\Windows\JobComplete.txt
echo Please close this file and turn off the computer. >>X:\Windows\JobComplete.txt
echo. >>X:\Windows\JobComplete.txt
echo Date: %TimeStamp% >>X:\Windows\JobComplete.txt
echo Serial: %serial% >>X:\Windows\JobComplete.txt
echo Vendor: %compvendor% >>X:\Windows\JobComplete.txt
echo Model: %compname% >>X:\Windows\JobComplete.txt
echo CPU Type \ Speed: %CPUname% >>X:\Windows\JobComplete.txt
echo Memory: %Memory%MB >>X:\Windows\JobComplete.txt
echo HDD Size: %hdd%GB >>X:\Windows\JobComplete.txt
REM End of Script
JobComplete.bat (Very Simple, just calls the JobComplete.txt file)
Echo off
REM Launched JobComplete.txt that was created in the WipeProcess.bat
X:\Windows\JobComplete.txt
Task Sequence: (Boot image is WinPE x64)
- Disable Bitlocker if starting from Windows & Reboot to PE
- Partition if Necessary (Copied from MDT TS)
- Bios Settings – Wipe Bios Password
- Wipe Drive (KillDisk)
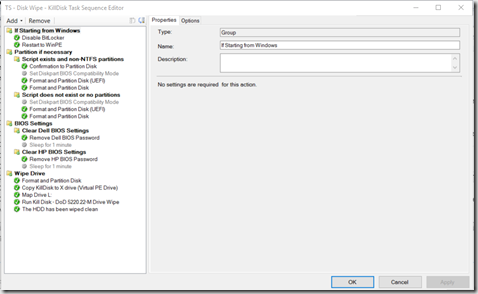
I’m going to focus on the Wipe Drive section
- Format and Partition Disk
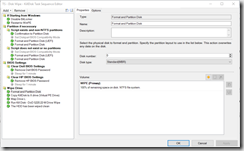
- Copy KillDisk to X drive (Virtual PE Drive)
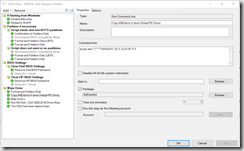
- Map Drive L (Used for log files)
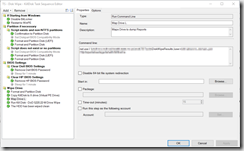
- Run Kill Disk
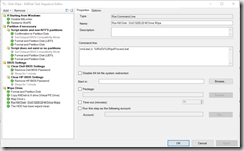
- The HDD Has been wiped clean (Notification on Screen)
JobComplete.bat –> Launches JobComplete.Txt File created during WipeProcess.bat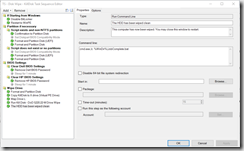
In Action
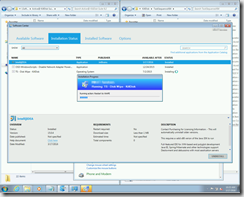
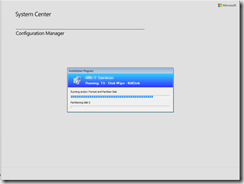
Warning to remove the bootable Flash Drive.. (IT will securely wipe that too)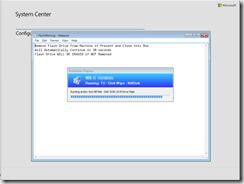
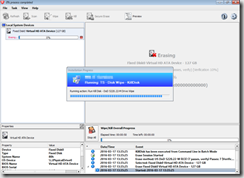
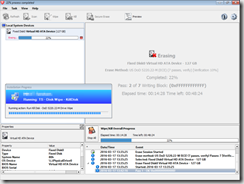
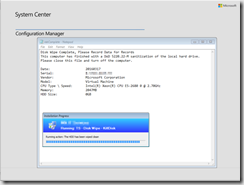
Sorry, my VM doesn’t provide the best results for the demo, but it’s much easier to grab the screenshots. Should give you the overall picture of the Task Sequence.
File Server Share Logs:
killdisk.log:
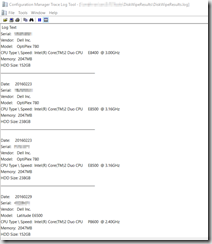
creates a page to print out to place on computer:
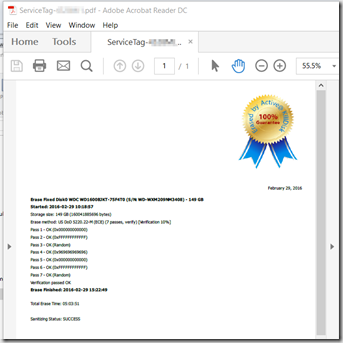
The Active Kill disk Certificates: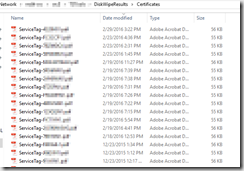
Hope those of you with Active Kill Disk find this useful.
Hi;
Thank you for this post. I’ve tried doing this but it spits out a R6034 error. Seems like it’s not loading a C run-time library properly or a something is missing that needs to be added into the WinPE?
I’m not doing the .bat script since I’m running this directly from MDT.
– WinPE x86 (Tested with x64 gives wrong arch error)
– WinPE Extra Directory to Add: Windows\System32\* (added all KillDiskFiles to the WinPE System32 path) tested launching killdisk.exe directly from WINPE CMD and it works.
Still getting that R6034 manually or via the task. What library or configuration should I do? If you have gotten this before and have a solution it would awesome if you could share.Thanks!
Hey Michael, what version of Active Kill Disk are you on?
I have not seen that error. We do have additional components in our Boot Image, but for our OSD, not sure if those impacted this or not.
Nothing has changed in my process since the post, other than I’ve added Print Support, so it prints a report when it’s done.
The Fact that you can launch killdisk.exe from the command prompt in WinPE x64, should mean that everything else should work.
Can you run this from command prompt after you run the xcopy command? cmd.exe /c %WinDir%\killdisk.exe -ea -em=3 -bm -fp
If that works, I’d test running that same syntax in a Run Command Step, and see what happens.
Hi, thank you for your quick reply. I’ve tested with version 9.0.1.5(doesnt run on x86WinPE) and version 10.0.6.0 (with both x86/x64) and I’m still getting that error.
WinPE is configured to have similar options to the one you mentioned for SCCM.
Version of ADK is 10.1.15063.0 which is were MDT 6.3.8443.1000 on a 2012 R2 Standard is pulling to create the custom wim.
Yes, running killdisk.exe from the CLI is possible but also with the error. (Note* I get error R6034 and then 0xc0000142).
I have attached screenshots to my public google drive folder since I can’t (or don’t know how to attach screenshots).
https://drive.google.com/open?id=0B_s9JXEzxLfsQlZwemUzUHJlRU0
Question, you are using xcopy to copy the content into the C:\Windows folder and not the System32 folder. Will try that with cmd.exe /c %WinDir%\killdisk.exe -ea -em=3 -bm -fp.
Update: WOW! It worked from %WinDir% !!! amazingg!! thank you so much!!!!!!!! I will folllow along this blog of yours. Seems like you have some useful Windows tips! – even tho I’m a Linux Admin, having from Win Admin on the web is always healthy 😉
Hi I stumbled upon this post and love it. I have actually implemented everything as you said and i can get it to launch fine.
The issue is , it launches and says it is the free version and not the registered version as is installed on the server (where i took the source files after installing and registering).
Is there any tips or tricks to get it working in winpe with full license and registration? as im stumped
I didn’t have to do anything besides the steps above. I don’t have access to the new version, which maybe activates slightly different now. Perhaps a registry key is needed now too. Wish I could be of more help.
Hi Gary,
Thank you for the post it was most useful with the implementation, I’m currently experiencing x2 issues and wondered if you could provide guidance.
1) The KillDisk application isn’t registered on boot can you advise where to implement the license key
2)With the export of log’s would it be possible to create a variable folder (Computer Name) so the log files and cert are stored within.
1 – All I did was install the software on a VM, make sure it was then activated and working properly, once I confirmed the software had been activated on the VM, I grabbed the content of the folder. That used to be enough to make the process work, I haven’t tested with the latest version of KillDisk.
2 – You can’t user computer name, you’re in WINPE, and it has no idea what the computer name is, you’d have to use SERIAL Number or something. I would try modifying a few lines:
-For the Cert: copy x:\*.pdf l:\%serial%\Certificates\ /Y
-For the log: Change this entire section: REM Creates Network Label for Machine – (L:\DiskWipe-SerialTag.txt) – Print & Fillout and Tape to Physical Machine to add %serial% so it is l:\%serial%\DiskWipe-%servicetag%.txt)
Note, if you’re using ConfigMgr to WIPE These, and the machines are still in ConfigMgr, you might be able to pull the name though configmgr, but then you’re adding extra complexity, and you’d have to make sure the computers that you wipe are all still in ConfigMgr. I deployed this TS to unknown machines, because the machines had been long removed from ConfigMgr before we got around to wiping them.
Were you able to find a way of Activating it on newer version (Killdisk 12) .
I no longer have access to this. New Job a few years ago so I haven’t touched it since. I’d reach out to Active Kill Disk support and explain what you’re doing and see if they can provide guidance.
Hi, great article, im a little late i guess but i have this error.
error code 0x800700A1 xcopy killdisk to x drive virtual pe driver
im using the same TS as you.
TIA